Key Takeaways:
- Piracy not only causes significant revenue loss but also increases the risk of malware and compromised systems.
- Techniques such as DRM, product activation, and code obfuscation help prevent unauthorised access and distribution.
- Cloud-based services and subscription models enhance security through centralised control and continuous updates.
The world is shifting to a state where resources and information are available in just a click due to the rapid development in technology. This ease of use makes it much simpler for counterfeiting and software piracy to occur.
The Internet has made it exceedingly effortless to circulate software that has been made illegally. This spreads rampant piracy that is exceedingly irresponsible erodes the hard work done by creators and developers.
This phenomenon inhibits the software industry from generating revenue, ultimately stunting any possible growth or innovation in the field.
Luckily, the Indian Copyright Act provides recourse to most of these problems and manages to properly compensate creators of such software.
Developers and consumers both benefit from the usage and perceivals of the Act since it establishes a legal system to deal with cases of unauthorised usage.
This article aims to shed some light on ‘software piracy protection in India,’ the legal circumstances, and how one might protect their intellectual property in the digital realm.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Software Piracy and Intellectual Property Rights Protection
Software piracy is the unauthorised copying, distribution, or use of copyrighted software without the proper permission or license from the software’s creator or publisher.
This can include activities such as
- making multiple copies of a single software license,
- distributing software without a valid license,
- downloading pirated versions from the internet, or
- using a single licensed copy on multiple computers without the appropriate multi-user license.
Software piracy is illegal and can lead to legal consequences for both the distributor and the user.
To begin with, it cripples the income potential of the software developers and in addition, poses a security threat to the users as pirated software lacks official updates and contains malware or viruses.
In India, software falls under the category of programs protected by copyright laws and unlawful use of such programs is stored as theft.
At the same time, making backup copies of the software for personal use is legal. However, any form of backup that violates the proprietary rights of the owner can subject them to prosecution.
Intellectual property speaks about everything created using one’s brain and is entitled to legal protection from the use of others without consent.
The range of intellectual property encompasses patent, copyright, trademark and trade secret. The rights give the owner the right to economic control of their work for a set duration.
India is a party to the TRIPs agreement, which caused a revision of the country’s laws to offer extensive protection of intellectual property. Software is treated as a work of Indian nationality and is an object of protection under “The Copyright Act of 1957”.
Factors Behind Software Piracy in India

Software Availability Conflicts
The digitisation has moved beyond just replacing manual chores with modern marvels. It has also ensured that a vault of information is accessible with the click of a button.
While the advancements in technology are greatly beneficial, they do come with a set of complications especially regarding cyber law and intellectual property abuse.
The Indian Copyright Act of 1957 and the Information Technology Act of 2000 provide protection for software programs instrumental in this digital transformation.
However, the availability and accessibility of these digital assets have further plagued the problem of software piracy.
Software is created with a myriad of programming languages that tell a computer to perform certain tasks in a specific order.
These software products can broadly be divided into system software, application software, and programming software.
While some of these programs can be downloaded and utilised freely, others require a purchase or a license.
The act of unauthorised reproduction or distribution of a licensed software is referred to as as piracy.
The illegal reproduction of software has become easier with the enhancement of the internet, making the prevention of such acts increasingly difficult.
The Internet has Impacted Piracy
It’s a common misconception that software piracy is solely a byproduct of the digital age.
In reality, there were times when software was predominantly sold bundled with hardware, simplifying the process of making illegal copies.
However, as technology evolved, software started being sold as standalone products, inadvertently increasing the instances of piracy.
The 1980s saw the Internet making its mark, ushering in novel forms of piracy.
Bulletin Board Systems (BBS) became the go-to platforms for software pirates, enabling them to upload and download counterfeit software, thus promoting unauthorised distribution.
As the internet landscape transformed, so did the methods employed by software pirates.
The advent of systems like File Transfer Protocol (FTP) further simplified the sharing and distribution of counterfeit versions.
Recognising the gravity of the situation, organisations like the Business Software Alliance (BSA) sprang into action to combat software counterfeiting and to foster a lawful ecosystem for software products.
In this digital age, copyright holders and content owners face an uphill battle against online piracy.
The illegal copying of digital files, be it software or other digital content, infringes upon the rights of these owners.
Unlicensed software, often distributed by pirates, poses a significant threat to the intellectual property rights of original creators.
It’s imperative for users to recognise the value of legal version and steer clear of counterfeit software to ensure that the rights of content owners are upheld.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
BSA’s Stance on Global Software Piracy and Its Role
The Business Software Alliance (BSA) reports that globally, around 36% of the software currently in use is pirated.
BSA is a non-profit trade association established to champion the objectives of the software sector and its associated hardware entities.
Representing the global commercial software industry and its hardware allies, BSA communicates their perspectives to governments and within the global market.
Its membership roster boasts prominent names like Adobe, Apple, Autodesk, Microsoft, Symantec, and many others.
A significant part of BSA’s mission is to assist its members in combating software piracy.
Software Piracy Protection in India

Indian Copyright Act of 1957
In India, the Copyright Act of 1957 empowers the country to combat software piracy by implementing both civil and criminal laws.
The range of sentence for those who are guilty of software copyright infringement is from a minimum of seven days to a maximum prison term of three years.
Moreover, fines may be set anywhere between 50,000 and 200,000 rupees. In some cases of piracy offenses, the provisions of Information Technology Act, 2000 may also apply.
Under Act of 1957 Section 13 (1) (a) of Indian Copyright Act categorises computer programs as an original work of literature which is protected as an author’s intellectual creation.
Many civil and criminal liabilities arise from violating these works. The 1994 amendment to the Act makes it an offence to use copyrighted software without proper authorisation.
Denying the rights associated with the said works is considered infringement for which the Author or the owner can pertain to the law as there are established consequences for such actions.
In order to enforce protections against the unlawful copying of copyrighted software, the Act provides for injunctions, orders for recovery of damages and other administrative sanctions imposed by relevant authorities.
Section 51 (a) (ii) of the Act goes further to state that copyright infringement occurs when a person uses a place for making available to the public through any means, computer program or other works for commercial purposes.
The term “communication to the public” is defined in Sec. 2(ff) of the Act as the act of listening to, enjoying, or viewing copyrighted content. However, the Act doesn’t explicitly address the liabilities of Internet Service Providers, unlike some other countries.
Furthermore, the Act holds individuals, groups, and companies accountable for providing internet services, as well as directors, either individually or collectively, who authorised the infringement.
A distinct section in the Act addresses the “offense” of using or aiding the use of copyrighted content, penalising both the user and those assisting in the infringement.
Section 69(1) of the Act emphasises that anyone involved in the management or operations of a company will face penalties if they use or assist in the unauthorised use of copyrighted content.
Information Technology Act, 2000: A Closer Look
The Information Technology Act of 2000 serves as a significant tool against the rampant infringement of copyrighted software. Section 2(w) of the Act encompasses all Internet service providers and other intermediaries.
This includes entities like cybercafés, auction sites, online payment platforms, search engines, and more, which receive, store, and provide records on behalf of another individual.
However, the Act doesn’t clearly define the extent or amount of liability that can be imposed on these service providers.
They can be exempted from certain sections if they can demonstrate a lack of knowledge about the offense or if they’ve taken reasonable measures to prevent such offenses.
The Act categorises the services provided by Internet Service Providers into three types: transmission of third-party information, links hosted by the providers, and storage of third-party data.
This legislation essentially offers a protective shield for search engines and Internet Service Providers, allowing them to distance themselves from third-party content.
This, in turn, absolves them from the responsibility of implementing stringent measures to curb piracy. However, the Act falls short when it comes to addressing situations where a service provider is alerted about the use of pirated content on their platform.
To claim exemption, providers must prove that they neither initiated, received, nor altered any transmission of the work.
The Ministry of Communication and Information Technology has introduced mandatory guidelines outlining the due diligence required by intermediaries during the transmission of work.
These guidelines, which subscribers must also adhere to, are outlined under Section 79 of the Act, 2000.
Rule 3(4) of the Act stands out as a beneficial provision for copyright owners.
It mandates the removal of pirated content from services once identified and communicated to the respective service provider. Failure to comply can lead to legal action against the service provider.
Organisations in India Combating Copyright Infringement
India has a limited number of institutions and organisations at the state level dedicated to combating the issue of piracy.
However, at the national level, the National Association of Software and Service Companies actively battles against software piracy.
Additionally, there’s a proposal to establish a National Cyber Corp Committee, which aims to assist the government, judiciary, and quasi-judicial bodies in addressing and reducing software piracy.
Judicial Stance on Copyright Infringement in India
Indian courts have been proactive in safeguarding copyrighted computer programs.
Drawing insights from verdicts in the USA and European nations, they have awarded substantial damages to aggrieved parties.
For instance, in the 2006 Microsoft case, the Delhi High Court recognised the defendant’s infringement of copyrighted products like Microsoft Office 2000 and Microsoft Office 9.
The court emphasised the pressing need to combat piracy, given the escalating instances of copyright violations, and consequently ordered the defendant to pay significant damages to Microsoft.
In the renowned case of Super Cassettes Industries v. Yahoo Inc., the plaintiff argued that Yahoo had violated their copyrighted content via its portal.
The court responded by issuing an injunction, preventing Yahoo from reproducing and transmitting the plaintiff’s copyrighted material on its platform.
Another case, Microsoft Corporation v. Mr. Kiran and Anr., saw the court highlighting the growing threat of software piracy in India and the urgent need for robust laws to deter such infringements.
In certain instances, courts have even directed service providers to abstain from using, storing, receiving, and selling copyrighted content on their platforms.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
7 Software Piracy Protection System
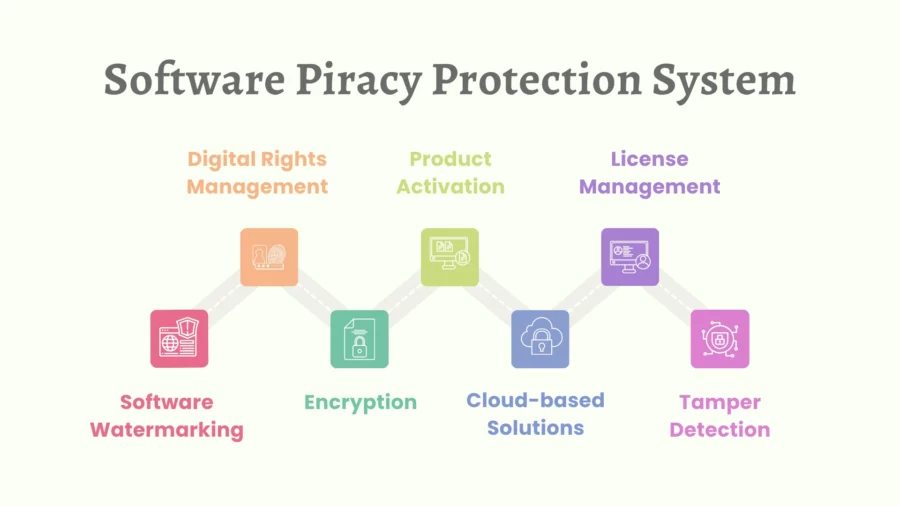
Software theft is a concern which inflicts massive damages on developers, publishers, and businesses. It consists of the unauthorised reproduction, selling, or usage of software that is protected by copyright.
To resolve this issue, developing an effective software piracy protection application is crucial.
Consider the seven most important solutions at hand for combating piracy:
1. Digital Rights Management (DRM)
This technological solution is utilised by publishers and copyright owners in order to restrict usage of their internet content to determine whether it has been pirated.
This minimises the use of illegal software as it assures that only authenticated users can avail themselves to the software and use it.
2. Product Activation
An authentic product key or serial number must be provided before the application can be fully utilised.
This helps in assuring the proper use of the software so that it does not get registrar on more machines than what is allowed per the license, thus supporting software piracy protection.
3. License Management
License management tools are utilised by other software companies in order to gauge compliance with the end-user license terms.
These tools guarantee that the purchased license is respected when it comes to software usage, whether it’s single-user, multi-user, or network versions.
4. Software Watermarking
This involves embedding a unique code or data set into the software.
This watermark helps trace the origin of pirated copies, pinpointing sources of unauthorised distribution and reinforcing copyright ownership.
5. Encryption
By encrypting the software code, it becomes challenging for pirates to reverse engineer or create unauthorised copies.
Strong encryption acts as a shield, making the software tamper-proof and safeguarding it from malicious code.
6. Cloud-based Solutions
Offering software as a service (SaaS) reduces the chances of piracy.
Since users access the software online, it’s challenging to create unauthorised copies.
This approach also offers enhanced online security, as the software remains on the server, away from potential threats.
7. Tamper Detection
Advanced anti-piracy systems can identify if software has been altered. If modifications are detected, the software might become inoperative or notify the developer.
This is especially crucial in business networks where the distribution of software needs strict monitoring.
Additional Anti-Piracy Measures:
- Hardware-locked Software Key: Ties the software to a specific device, ensuring it can’t be used elsewhere.
- End-user Agreements: These agreements outline the terms of software usage, deterring end-user piracy.
- Security Monitoring: Monitors online channels for illegal activities related to the software.
- Authentication Server Checks: Validates the legitimacy of the software each time it’s used.
- Deep Packet Inspection Application: Monitors network traffic to detect and prevent the distribution of unauthorised copies.
- Anti-piracy Technologies: Incorporate various security features to deter digital piracy, from license code checks to malware attack prevention.
In essence, while no system is entirely foolproof, a combination of these measures can significantly deter software piracy.
By staying vigilant and continuously updating anti-piracy strategies, software companies can protect their intellectual property and ensure that only legitimate users benefit from their products.
What’s Next?
The risk of software piracy continues to loom large in our increasingly digital world, underscoring the importance of robust digital copy protection measures.
In this context, Bytescare emerges as a beacon of hope.
With its advanced digital piracy monitoring service, Bytescare offers unparalleled protection, ensuring that software remains in the hands of genuine users and away from the clutches of piracy.
By harmonising these strategies stated here in this article, and with the added assurance of Bytescare’s specialised services, we can ensure comprehensive protection against piracy, preserving the rights of creators and ensuring users benefit from genuine, secure software experiences.
For those seeking to fortify their software’s defenses, don’t hesitate to book a demo with Bytescare and witness the pinnacle of software protection firsthand.
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
What is software piracy protection?
It refers to the measures and techniques implemented by software developers and publishers to prevent the unauthorised copying, distribution, or use of their copyrighted software.
This protection can range from digital rights management (DRM) systems to product activation keys and encryption methods.
What are the regulations for software piracy protection under the Indian copyright act?
Under the Indian Copyright Act of 1957, provisions related to software piracy were introduced by the Amendment Act of 1994.
The Act now includes a definition of a ‘Computer Program’ and defines an infringing copy as one that is used without the license or permission granted by the copyright owner.
The Act also provides penal provisions under Section 63B, titled “Knowing use of infringing copy of computer programme to be an offence.” Violators can face both civil and criminal penalties, including fines and imprisonment.
What are the different types of software piracy?
Software piracy can manifest in various forms, including:
a. Softlifting: Buying a single licensed copy of software and then installing it on multiple devices, violating the license agreement.
b. Counterfeiting: Illegally replicating and selling software under the guise of authenticity.
c. Internet Piracy: Downloading software from peer-to-peer networks, file-sharing sites, or unauthorised websites.
d. Hard Disk Loading: Installing unauthorised copies of software on the hard drives of computers, which are then sold to unsuspecting customers.
e. Client-Server Overuse: More users on a network use a software than the license permits.
What is software piracy with example.
Software piracy refers to the unauthorised copying, distribution, or use of copyrighted software.
For example, if someone purchases a single-user license for a software program but then installs it on multiple computers for use by multiple people, that constitutes software piracy.
Another example is downloading a paid software program from an unauthorised or deceptive website or peer-to-peer network without purchasing it.
What are the consequences of software piracy?
While pirated software might come at a lower cost, it’s essential to understand the associated risks:
a. Increased chances of software failure or malfunction.
b. Lack of access to program support, updates, and customer service.
c. Absence of warranties and upgrade options.
d. Higher susceptibility to malware, viruses, and adware.
e. Slowed computer performance.
f. Legal implications due to copyright infringement.
What measures can users take to avoid supporting software piracy?
Users can steer clear of piracy by ensuring they download software only from reputable sources and purchasing or licensing software legally. This not only protects intellectual property rights but also ensures that users receive regular updates and support, reducing the risk of malware and other security issues.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.

