Key Takeaways:
- DNS spoofing involves altering a domain’s DNS records to redirect users to malicious websites, tricking them.
- Domain spoofing can compromise user data, steal credentials, and damage a brand’s reputation by mimicking trusted email domain.
- Employ DNSSEC, secure connections, and monitor DNS records to protect against spoofing and ensure website integrity.
Domain spoofing is a technique used by cybercriminals to deceive users by manipulating a website’s domain name system (DNS) records.
This allows attackers to make malicious websites appear as legitimate source, tricking users into providing sensitive information like passwords or credit card details. Domain spoofing is increasingly relevant as both individuals and businesses face growing threats from phishing, fraud, and identity theft.
Knowing how domain spoofing works is essential for businesses and individuals because these attacks can lead to significant financial losses, reputation damage, and data breaches.
For businesses, a spoofed domain can lead customers to fake sites that steal personal information or install malware. Individuals may unknowingly fall victim to these attacks, compromising their privacy and security.
Real-world examples of domain spoofing attacks highlight the severity of the issue. In 2020, hackers used domain spoofing to impersonate popular brands, tricking users into clicking on fake links and stealing sensitive data.
This illustrates the critical need for proactive measures, such as securing domain records, monitoring DNS settings, and using security protocols like DNSSEC to protect against these types of threats. How to spoof a domain? Awareness and vigilance are key to preventing domain spoofing from wreaking havoc!
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What is Domain Spoofing?
Domain spoofing is a type of cyberattack where hackers trick users by making a malicious website appear to be a trusted one.
They do this by altering the domain name system (DNS) records, which direct a user’s browser to a fake website that looks identical to the real one.
The goal is to deceive individuals into believing they are interacting with a legitimate site, which can lead to the theft of personal information like passwords, credit card details, or login credentials.
Attackers typically use domain spoofing for phishing, fraud, or distributing malware. For example, they might create a fake banking website that looks like the real thing, hoping users will enter their sensitive information.
Similarly, they may trick users into downloading malware disguised as software updates or other trusted files. These attacks can cause financial loss, data breaches, and long-term damage to a business’s reputation.
While domain spoofing involves creating fake websites, it is different from email spoofing, which targets users through fake emails. In email spoofing, attackers impersonate legitimate senders to gain trust and prompt users to take action, like opening attachments or clicking on malicious links.
Though both tactics involve deception, domain spoofing focuses on fake websites, while email spoofing primarily involves fraudulent emails.
Both forms of spoofing are serious cyber threats, and knowing how they work can help individuals and businesses better protect themselves from these potential threats.
Common Types of Domain Spoofing
| DNS Spoofing (Cache Poisoning) | Attackers manipulate the DNS cache to redirect users to malicious websites by corrupting DNS records. |
| Subdomain Spoofing | Cybercriminals create a fraudulent subdomain that looks similar to a legitimate one. |
| Typosquatting | Attackers register domains with slight misspellings of a legitimate domain. |
| Homograph Attacks | Attackers use characters from different alphabets that look similar to common letters in a domain. |
| Brand Impersonation | Hackers mimic an established brand’s domain, often using slight variations in spelling or adding extra words, to impersonate the brand’s site. |
| URL Spoofing | Attackers take advantage of loopholes in security to trick people into heading from a legitimate site to a fake one. |
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Why is Domain Spoofing a Threat?

Domain spoofing is a significant security threat because it allows attackers to deceive users into trusting fraudulent websites.
Cybercriminals can create fake sites that look exactly like legitimate ones by changing domain records or using similar-looking web addresses.
When users unknowingly visit these spoofed sites, they might enter sensitive information like passwords, credit card details, or personal data, putting their security and privacy at risk.
One of the most dangerous aspects of domain spoofing is that most people don’t even notice it. People tend to trust websites that look like the ones they know, and it can be hard to tell the difference between a legitimate site and a spoofed one.
This makes it easier for attackers to conduct phishing campaigns, steal identities, or distribute malware. For businesses, the consequences can be devastating, as customers may lose confidence in the brand, leading to reputational damage and financial losses.
Additionally, domain spoofing can be used to bypass security measures. Traditional methods of preventing cyberattacks, such as firewalls or email filters, may not always detect these deceptive websites. Since the spoofed domains look legitimate, users might not recognise the threat until it’s too late.
Since online transactions and communication are the norm, the impact of domain spoofing can be widespread. People can lose money, and businesses can get sued or lose customers’ trust.
Domain spoofing needs to be prevented in order to protect personal as well as organisational data.
How to Spoof a Domain?
Domain spoofing is a cyberattack technique used to deceive users by creating fraudulent websites that appear to be legitimate. Here’s a step-by-step breakdown of how domain spoofing works:
Identifying a Target Domain
- Attackers first choose a trusted domain, such as a bank, online store, or social media platform, which users often visit.
- They aim to impersonate this legitimate domain.
Manipulating DNS Records
- The next step involves manipulating the DNS (Domain Name System) records.
- Cybercriminals may use various methods, like exploiting vulnerabilities in the DNS system or engaging in DNS cache poisoning.
- By altering these records, attackers can redirect users to a fake version of the targeted website.
Creating a Fake Website
- Once the attackers have access to the DNS settings, they create a website that closely resembles the legitimate one.
- This could include using a similar domain name, identical design, and content to trick users into thinking it’s the real site.
Tricking Users
- The spoofed domain is often spread through phishing emails, ads, or other malicious links.
- Users, believing they are visiting the trusted website, may enter sensitive information, such as passwords, credit card details, or personal data.
Exfiltrating Data or Installing Malware
- Once users submit their information, attackers can steal it for identity theft or fraud.
- Malware could be installed on the user’s devices in some situations.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What Are the Risks and Impacts of Domain Spoofing?
| Data Theft and Identity Fraud | Attackers use spoofed websites to steal sensitive personal information like passwords, credit card numbers, and Social Security details. |
| Malware and Ransomware Attacks | Spoofed domains can be used to distribute malware or ransomware, infecting users’ devices or corporate networks. |
| Reputation Damage | Businesses targeted by domain spoofing risk losing customers’ trust when they fall victim to fraudulent sites. |
| Legal and Compliance Issues | Companies may face legal action if customer data is compromised due to domain spoofing, especially in regulated industries like finance or healthcare. |
| Financial Loss | Both individuals and businesses can face direct financial losses through fraud, theft, or paying for ransom in case of ransomware attacks. |
| Loss of Customer Loyalty | If customers fall victim to a spoofed site, they may lose trust in the brand, leading to a decline in customer loyalty and repeat business. |
How to Protect Against Domain Spoofing?
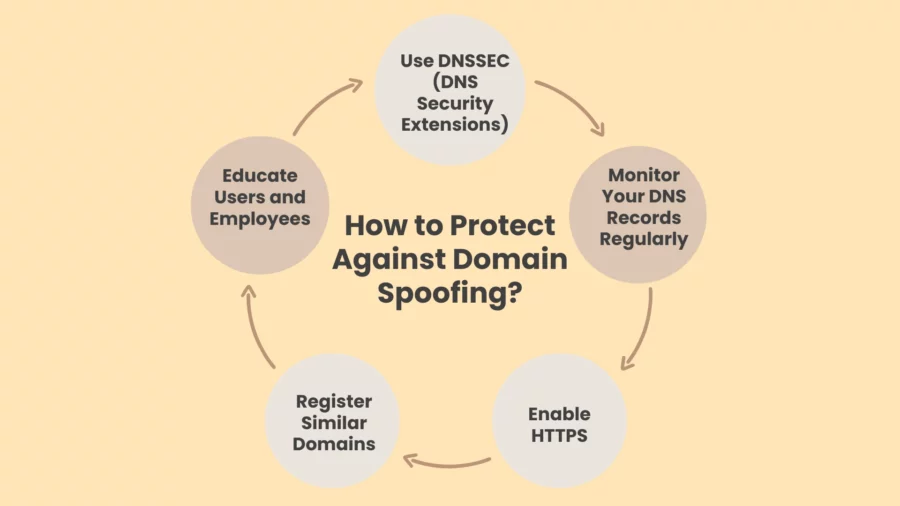
To keep personal and business information safe from cybercriminals, you need to protect against domain spoofing. To lower your chances of being a victim of domain spoofing attacks, here are some important things you can do:
Use DNSSEC (DNS Security Extensions)
DNSSEC adds an extra layer of protection to your domain by ensuring that DNS records are not tampered with. It helps verify that the DNS information is legitimate, making it harder for attackers to redirect users to fake websites.
Monitor Your DNS Records Regularly
Check your domain’s DNS records often for any changes that were not made by you. You can set up alerts to let you know when your domain settings are changed. In this way, you can act quickly if something suspicious occurs.
Enable HTTPS
Make sure your website uses HTTPS, which encrypts data transmitted between users and your site. Not only does this protect sensitive information, but it also signals to visitors that your website is secure, reducing the likelihood of them being tricked by a spoofed version.
Register Similar Domains
To protect against typosquatting or domain variations, consider registering similar domain names with common misspellings or extra characters. This prevents attackers from using these variations to deceive users into visiting fake sites.
Educate Users and Employees
Getting aware is key. Users and employees should be trained how to spot suspicious websites in addition to avoid clicking on links in unsolicited email messages. Encourage people to be careful when they enter personal information online.
Tools to Prevent and Detect Domain Spoofing
Domain spoofing can be prevented with a number of tools, adding an extra layer of security for individuals as well as businesses. Here are some important tools to think about:
DNSSEC (DNS Security Extensions)
DNSSEC is a vital tool for protecting against domain spoofing. It adds security to the Domain Name System (DNS) by digitally signing DNS data, ensuring that the information received by users is authentic and hasn’t been tampered with.
By enabling DNSSEC, you can significantly reduce the risk of attackers redirecting users to fake websites.
SSL/TLS Certificates
Using SSL/TLS certificates enables HTTPS on your website, which encrypts the connection between users and your site. This provides not only a secure browsing experience but also signals to visitors that your site is legitimate.
Attackers often avoid using HTTPS on spoofed sites, so it’s an effective way to spot fake domains.
Domain Monitoring Services
Tools like DomainTools and WhoisXML API help you monitor changes to your domain records, alerting you to unauthorised alterations.
Regular monitoring of DNS records ensures that any suspicious changes are detected early, preventing potential spoofing attacks.
Anti-Phishing Software
Anti-phishing tools, such as PhishLabs or Barracuda’s email protection, can detect phishing attempts and warn users about spoofed websites. These tools help identify harmful links in email content or on websites that may lead to fake domains.
DMARC, SPF, and DKIM
These email authentication protocols help prevent email spoofing, which often accompanies domain spoofing.
By setting up DMARC, SPF, and DKIM records, you can verify that email headers sent from your domain are legitimate, reducing the risk of attackers using email as a tool for domain spoofing.
What to Do If You Have Been Spoofed?
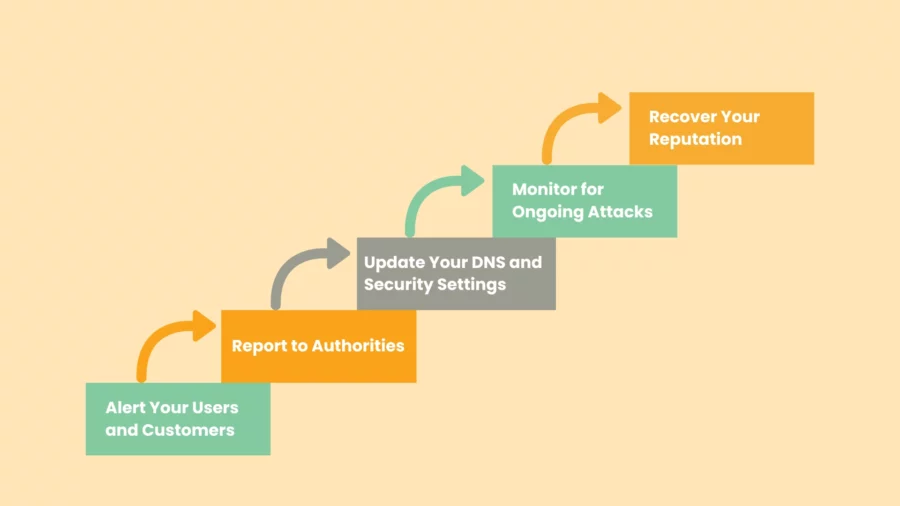
If you find out that your domain has been spoofed, you need to act right away to lessen the damage. Things you should do are these:
Alert Your Users and Customers
Notify your users, customers, and employees about the email spoofing attack as soon as possible. Inform them that a fake version of your website or domain is circulating and advise them not to interact with it.
Provide instructions on how to verify legitimate websites and email systems to avoid falling victim to the attack.
Report to Authorities
Contact your web hosting provider or domain registrar to report the malicious activities. Many providers can help mitigate the attack by disabling the fake domain or domain redirect.
Additionally, report the spoofing attack to authorities like the Internet Crime Complaint Center (IC3) or other relevant local authorities, especially if sensitive information has been compromised.
Update Your DNS and Security Settings
If the attack involved DNS spoofing, immediately update your DNS records and enable DNSSEC (if not already enabled) to prevent further redirection.
Review and strengthen your security settings, including implementing HTTPS and securing your domain with SSL/TLS certificates.
Monitor for Ongoing Attacks
Continue to monitor your domain and any other related domains for suspicious activity. Set up alerts for changes to your DNS records or website content. Use tools like DomainTools or other monitoring services to keep track of any new spoofed sites that may pop up.
Recover Your Reputation
Work on restoring your brand’s reputation. Communicate openly with your customers, addressing any concerns, and providing reassurance that you’ve taken steps to prevent future attacks. Implementing email security protocols and educating your users can help rebuild trust.
What’s Next?
While knowing how domain spoofing works is important for cybersecurity awareness, it’s essential to emphasise that engaging in domain spoofing is illegal and unethical.
The impact of such email phishing attacks can be devastating, leading to data theft, financial loss, reputational damage, and legal consequences.
Instead of focusing on how to carry out such fraudulent activities, it’s far more beneficial to learn how to protect your domain and prevent these attacks.
By implementing security measures such as DNSSEC, using SSL certificates, and educating users, businesses can safeguard their domains from potential spoofing.
Staying vigilant and proactive is the key to ensuring a secure online environment for both individuals and organisations.
Protecting your brand starts with asserting your rights. Bytescare’s Brand Protection Solutions simplify the DMCA takedown process, ensuring your identity and trademarks remain safe from unauthorized use.
We help safeguard your intellectual property and maintain your brand’s integrity. Contact us today to learn how we can protect your brand!
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
What is the difference between domain spoofing, email spoofing, and phishing?
Domain spoofing involves creating a fake website that mimics a legitimate one. Email spoofing involves sending malicious emails from a trusted domain. Phishing is the broader act of tricking users into sharing sensitive information, often using spoofed email address or websites.
How to spoof a domain name?
Domain spoofing is a malicious intent and illegal. It’s important to focus on protecting against spoofing by using domain spoofing security measures like DNSSEC, HTTPS, and monitoring your domain’s DNS records regularly to prevent unauthorised changes.
How can I tell if a domain is spoofed?
Look for subtle differences in the domain name, such as misspelled words or extra characters. Check for an HTTPS connection, and use domain validation tools to verify the legitimacy of the site. Be cautious if the email sender asks for sensitive information unexpectedly.
What is the difference between domain impersonation and spoofing?
Domain impersonation refers to using a similar domain name to mimic a legitimate one, often for phishing or fraud. Spoofing is a broader term, including both domain and email spoofing, where cyber criminals imitate actual sources to deceive users.
How to identify domain spoofing?
Look for mismatched or suspicious URLs, poor website design, and lack of HTTPS. Also, be cautious of unsolicited links in email content leading to websites that seem unfamiliar or ask for personal information.
What to do if you victimise domain spoofing?
Report the incident to your domain registrar and hosting provider immediately. Inform your users, change any compromised credentials, and strengthen your security measures, such as enabling DNSSEC and using HTTPS to prevent future attacks.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.

