Key Takeaways:
- Protecting a brand from exploitation is critical for maintaining trust, ensuring regulatory compliance, and supporting sustainable business growth.
- Brand Exploit Protection helps identify and mitigate threats like phishing, impersonation, and counterfeit products, safeguarding a brand’s reputation and consumer trust.
- Leveraging AI, machine learning, and automation enables real-time detection and swift response to brand exploitation across digital platforms.
A brand nowadays is not more than a face or a slogan: it’s far more complex for it symbolises the identity of an enterprise that represents the confluence of summation of cumulative customer experiences with perceptions.
Thus, creating a brand consumes a huge time, resources as well as very importantly creativity. But that same digital marketplace offering unparalleled opportunities for brand building also creates tremendous risks.
Brands will always be exposed to different frauds, such as counterfeits and reputation misuse. This calls for a very proactive and all-rounded approach toward “Brand Exploit Protect”: a framework or strategy that encompasses the many ways in which brand assets can be leveraged by mitigating potential risks and ultimately protecting brand integrity.
This article will look into the multi-faceted aspects of Brand Exploit Protect: the many forms of brand exploitation, the legal and technological tools available for protection, and the strategic considerations in building a resilient brand in the digital age.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What is Brand Exploit Protect and Why is it Important?
Brand Exploit Protection refers to several proactive steps and technologies set in motion to monitor, mitigate, and avoid exploitation of a brand’s identity, reputation, and intellectual property in the virtual world.
The technique generally used involves digital channel monitoring, fraudulent activity detection, and countermeasures against the impersonation of the brand, phishing campaigns, spoof websites, or any kind of counterfeited product that might damage the brand.
Why is Brand Exploit Protection Important?
The rise in digital commerce and online engagement has made brands exposed to a large number of risks. The risks compromise the brand’s reputation and the consumers’ trust as well.
Key reasons why Brand Exploit Protection is a critical factor:
Phishing Attacks
One of the most-if not the top-methods used by cybercriminals against brand exploitation up to date has been phishing.
Attackers masquerade as a legitimate brand in order to trick targeted users into making bad disclosures of sensitive information, whether that be user logins or even credit cards, among personal data.
Brand Impersonation
These fraudsters create fake websites, social media profiles, or email addresses impersonating a brand. These impersonations are then used to deceive customers, destroy the brand’s image, and divert traffic or revenue.
Loss of Consumer Trust
When customers are made victims of a scam related to any brand, their confidence shrinks toward the brand. Such reputation damage can be for the long term and may result in less customer loyalty.
Counterfeit Products
Counterfeit goods sold in the name of a particular brand can damage its reputation, reduce sales of genuine products, and even put consumer’s lives at risk.
Regulatory Compliance
In the course of protecting customers from scams and fraud associated with their brand names, brands often get held liable. Failure to do so can also result in certain legal and regulatory consequences.
Why Protect a Brand from Exploit?
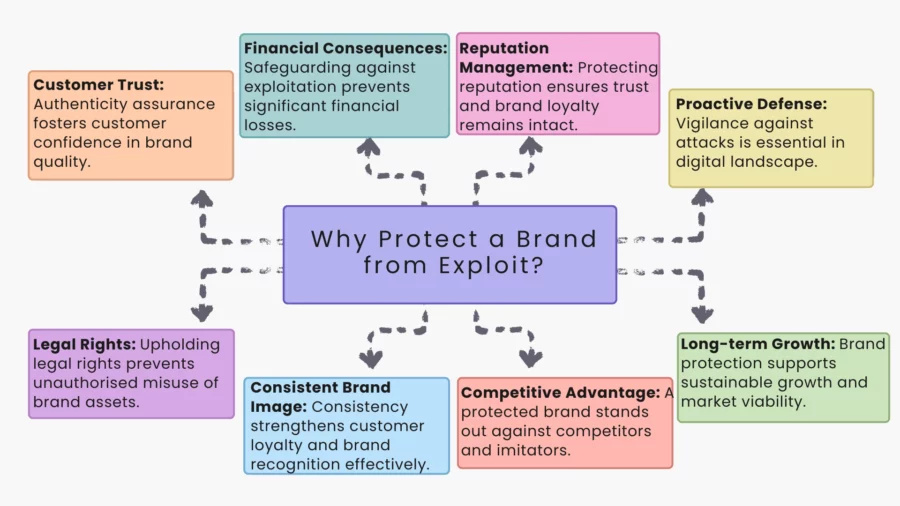
Reputation Management: Reputation is one of the mainstays a brand possesses.
Its exploitation, specifically through impersonation attacks engendered through malicious domains by unsophisticated attackers, would tarnish it and may lead to consumer trust issues. It ensures your brand remains positive and trustworthy in the public’s eye.
Financial Consequences: The major variety of brand exploitation includes counterfeiting of brand products and services, or brand-based attacks; these may wield heavy financial losses.
Protection of the brand ensures continuity of revenues and avoids possible financial losses that such malicious efforts may perpetrate.
Customer Trust: When customers buy a particular product or service, they have a certain amount of trust in the quality and authenticity of that product or service.
Phishing attacks are one of the most common attack vectors wherein the customers are tricked into purchasing low-quality or fake products in the name of a well-renowned brand. Such cases undermine their confidence in the brand.
Legal Rights: Brands have legal rights to their name, logo, and other intellectual properties. Protecting the brand would mean upholding these rights so that no unauthorised entity, especially malicious domains, could misuse them.
Consistent Brand Image: A consistent brand image builds a loyal customer base. Exploitation, especially through unsophisticated attackers using varied attack vectors, will result in mixed messages and confusion for consumers, diluting the brand’s essence and values.
Competitive Advantage: A well-protected brand enjoys a uniqueness in the marketplace; customers are able to recognise it and tell it apart from competition or imitations. This advantage places them ahead of those who have fallen victim to phishing attacks or other brand-based attacks.
Long-term Growth: Brand protection against exploitation, such as impersonation attacks and other malicious efforts, sustains the brand’s long-term viability in the market. It paves the way for further growth and expansion opportunities unhindered by threats from unsophisticated attackers.
Basically, in this digital world where every other second a new attack vector crops up, it becomes highly crucial for brands to be observant and take proactive steps for their defense mechanisms.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
5 Common Forms of Brand Exploitation
- Counterfeiting: This is one of the most prevalent forms of brand exploitation. Counterfeiters produce fake products that imitate genuine ones, often of inferior quality, and sell them under the name of a well-known brand. This not only deceives consumers but also damages the brand’s reputation and can lead to significant financial losses.
- Phishing Attacks: Cybercriminals create fake websites or emails that closely resemble a brand’s official communication channels. The goal is to deceive users into providing personal information, such as login credentials or credit card details, under the pretense of interacting with the genuine brand.
- Trademark Infringement: This involves the unauthorised use of a brand’s trademarked name, logo, or other intellectual properties. It can mislead consumers into believing there’s an association or endorsement where none exists, leading to confusion and potential brand dilution.
- False Advertising: Some entities may make false or misleading claims about a brand or its products, either to promote a competing product or to tarnish the brand’s image. This form of exploitation can misguide consumers and harm the brand’s credibility.
- Unauthorised Merchandising: This involves producing and selling merchandise, such as clothing or accessories, featuring a brand’s logo or name without obtaining the necessary licenses or permissions. It capitalises on the brand’s popularity without providing any compensation or benefits to the brand owner.
In interconnected world, brand exploitation can take many forms, making it crucial for businesses to remain vigilant and proactive in protecting their brand’s integrity and value.
Steps for Brand Exploit Protection
- Trademark Registration: Secure your brand name, logo, and distinctive signs by registering them. This not only grants legal protection against unauthorised use but also acts as a defense to offense strategy against potential infringers.
- Continuous Monitoring: Utilise a combination of machine learning tools to track online mentions and detect any unauthorised, malicious, or active attacks related to your brand promptly.
- Employee Awareness: Educate your team about brand exploitation risks, including the nuances of cyber attacks and takedown attacks. Equip them with the knowledge to recognise and report suspicious activities proactively.
- Digital Asset Security: Adopt a pervasive security approach for your website, social media, and other online platforms. Use secure hosting, SSL certificates, robust passwords, and gateway defenses to ward off potential threats.
- Legal Recourse: In the face of unauthorised brand use, act swiftly. This includes sending cease-and-desist letter or pursuing legal action when necessary, transitioning from a proactive defense stance.
- Customer Engagement: Maintain open communication with your clientele. Alert them about potential scams, active attacks, and guide them on making authentic product purchases.
- Use Anti-Phishing Tools: Implement tools, backed by a combination of machine learning, that can detect and prevent phishing and other cyber attacks, especially if you operate an e-commerce platform or online service.
- Collaborate with Platforms: Partner with online marketplaces and social media platforms to report and swiftly remove counterfeit products or fake accounts that misuse your brand, effectively countering takedown attacks.
- Stay Updated: As exploitation tactics and cyber attack methods evolve, stay informed about the latest threats. Adapt your protection strategies accordingly, ensuring a proactive defense against emerging challenges.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What’s Next?
In digital age, the value of a brand reputation cannot be overstated.
Recognising the significance of the brand protection from exploitation, and acting preemptively, is the key to ensuring your brand’s enduring strength, reliability, and success in the discerning eyes of consumers.
Bytescare comprehends this critical need, offering premier trademark enforcement solutions, supercharged by cutting-edge AI technology.
Their comprehensive strategy not only promptly identifies violations but also keeps a vigilant watch on real-time activities, ensuring all-encompassing protection, spanning platforms from social media to potential phishing websites.
Don’t leave your brand’s digital presence to chance; fortify it with Bytescare’s brand protection service. Ready to shield your brand? Book a demo today.
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
Write five benefits for brand protection services.
5 benefits are as follows:
a. Identifies unknown attack patterns.
b. Safeguards brand reputation.
c. Reduces financial losses.
d. Enhances customer trust.
e. Streamlines legal recourse.
What is brand protection?
Brand protection encompasses the measures taken to safeguard a brand’s identity, reputation, and intellectual property from infringement, misuse, or damage. This includes legal protections, reputation management, and proactive strategies to mitigate risks.
What is the first step in brand protection?
The first step is to trademark your brand name and logo, giving you legal rights to them.
How can I monitor my brand online?
There are several tools and services available that track online mentions of your brand and alert you to potential issues.
What if someone is spreading false information about my brand?
Engage with the individual, address the misinformation, and consider legal action if necessary.
Can I prevent all forms of brand exploitation?
While it’s challenging to prevent all forms, with vigilance and the right strategies, you can significantly reduce the risk.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.


