Key Takeaways:
- Content protection is essential to prevent content theft and maintain online brand integrity
- Technical methods, such as disabling right-click functionality, can help prevent content copying
- Legal protection strategies, including copyright registration, can provide additional safeguards for your digital content
As a digital content creator, keeping your work safe is key. Protecting your content stops others from copying it. This keeps your brand strong online. It also helps avoid losing money and damaging your reputation.
Comprehending the need for content protection is important. It helps keep your digital content safe. This guide will show you how to protect your work. You’ll learn how to stop others from using it without permission.
Protecting your content needs both technical and legal steps. Knowing why it’s important helps you act fast. This guide will teach you how to protect your content from being copied. You’ll learn about technical ways to stop copying, legal steps, and website settings.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What is Content Plagiarism and Why it Prevails?
Content plagiarism is the act of taking someone else’s work – be it text, images, videos, or even code – and presenting it as your own without proper attribution. This can range from verbatim copying to subtly rephrasing content while maintaining the original structure and ideas.
Plagiarism not only violates ethical standards but can also have severe legal consequences, particularly for copyrighted material.
Why Do People Steal Content?
Content theft, unfortunately, stems from a variety of motivations, some driven by expediency, others by malicious intent. Often, plagiarism is simply a shortcut.
Creating high-quality, original content takes time and effort. For some individuals and organisations, stealing content is a quicker, cheaper way to populate a website, social media feed, or even academic paper. This can be especially tempting for those under pressure to produce large volumes of content quickly.
Another key driver is the desire for online visibility and improved search engine rankings.
Stolen content, especially if it’s already popular and well-ranked, can be used to artificially boost a website’s search engine optimisation (SEO). This unethical tactic attempts to gain an unfair advantage in search results, diverting traffic and potentially revenue away from the original creator.
Beyond these motivations, content theft can also be fueled by:
- Financial gain: Some plagiarists use stolen content to drive traffic to their websites and generate advertising revenue. Others may sell stolen intellectual property directly.
- Malicious intent: Content theft can be used to damage the reputation of the original creator, spread misinformation, or even sabotage a competitor.
- Lack of awareness: In some cases, individuals may simply be unaware of copyright laws and proper attribution practices. While this doesn’t excuse plagiarism, it highlights the importance of education and clear copyright notices.
Identify the Different Types of Content Vulnerable to Theft
A wide range of content is susceptible to theft in the digital marketplace. Essentially, any original creative work can be targeted. Here’s a breakdown of common types:
- Written Content: This encompasses articles, blog posts, website copy, books, ebooks, research papers, poems, scripts, and code. Text-based content is easily copied and pasted, making it particularly vulnerable.
- Visual Content: Images, photographs, infographics, illustrations, designs, logos, and even presentations can be readily downloaded and reused without permission.
- Audio Content: Music, sound effects, podcasts, audiobooks, and lectures are all susceptible to unauthorised duplication and distribution.
- Video Content: Movies, television shows, online courses, tutorials, vlogs, animations, and any other form of video recording can be illegally downloaded, re-uploaded, or embedded elsewhere.
- Software and Code: This includes applications, games, plugins, operating systems, and the underlying source code that powers them. Software piracy and code theft are significant concerns in the tech industry.
- Design and 3D Models: Architectural blueprints, product designs, CAD files, 3D models, and other design assets can be stolen and used for counterfeit products or competing designs.
- Databases and Data: Structured datasets, customer lists, market research, and other proprietary data compilations are valuable targets for theft, potentially leading to competitive disadvantages and privacy breaches.
- Online Educational Materials: Course content, quizzes, assignments, and other learning resources created for online education platforms are frequently targeted for unauthorised sharing and resale.
Any original creative work, regardless of format, should be considered at risk and protected accordingly.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Content Theft and Its Impact on Your Business

Content theft is a big problem for businesses. It makes original work less valuable. Protecting your content is key to staying ahead and growing.
| Type of Content Theft | Description | Impact on Business |
|---|---|---|
| Unauthorised Copying | Reproducing and distributing content without permission. | Revenue Loss from reduced sales, diluted brand value, and potential legal expenses. |
| Plagiarism | Stealing written content and presenting it as original. | Reputation Damage, loss of credibility, and possible SEO penalties from search engines. |
| Image Theft | Using images without proper authorisation or licensing. | Legal Liabilities due to copyright infringement, financial penalties, and loss of trust. |
| Software Piracy | Unauthorised use, duplication, or distribution of software. | Decreased Revenue, increased support costs, and potential security vulnerabilities in pirated versions. |
| Video/Content Scraping | Extracting and republishing video or other online content without consent. | Traffic Diversion away from original site, ad revenue loss, and brand dilution. |
| Theft of Trade Secrets | Stealing proprietary information, processes, or strategies. | Competitive Disadvantage, loss of market position, and intellectual property loss. |
| Deepfake and Synthetic Media | Creating misleading or fake content using advanced technologies. | Brand Reputation Risks, potential misinformation, and consumer distrust. |
| Link Hijacking | Redirecting legitimate links to unauthorised or malicious sites. | SEO Impact, traffic loss, and potential brand harm due to association with malicious content. |
| E-book and Digital Content Theft | Illegally distributing e-books, articles, and digital publications. | Reduced Sales, publisher revenue loss, and author royalties being affected. |
| App Piracy | Cracking and distributing paid applications for free use. | Loss of Revenue, decreased incentive for development, and potential security risks for users. |
How to Protect Your Content From Being Copied?
Protecting your digital assets is important. Using strong content protection tools can greatly lower the chance of unauthorised copying and sharing.
Copyright Notice
Explicitly declare your copyright ownership with a clear and prominent notice on all your content. This typically includes the copyright symbol (©), the year of publication, and your name or business name.
A robust copyright notice acts as a deterrent to potential infringers and formally establishes your legal claim to the work. This visible declaration makes it clear that the content is protected and unauthorised use is prohibited.
Properly displaying this notice reinforces your rights and strengthens your position in case of infringement.
Terms of Use
Establish clear and comprehensive terms of use on your website, outlining the permitted and prohibited uses of your content. Specify what actions users are allowed to take, such as sharing with attribution or using excerpts for educational purposes.
Clearly define restrictions, like commercial use or republication without permission. Well-defined terms of use provide a framework for acceptable content usage and strengthen your legal standing in case of disputes.
Watermarking
Apply visible or invisible watermarks to images and videos. Visible watermarks deter theft by overtly marking the content as yours and making it less attractive for unauthorised use.
Invisible watermarks, embedded within the file’s data, can be used to track and identify the source of pirated copies, providing evidence of ownership in infringement cases. Watermarking serves as both a deterrent and a tool for tracing unauthorised usage.
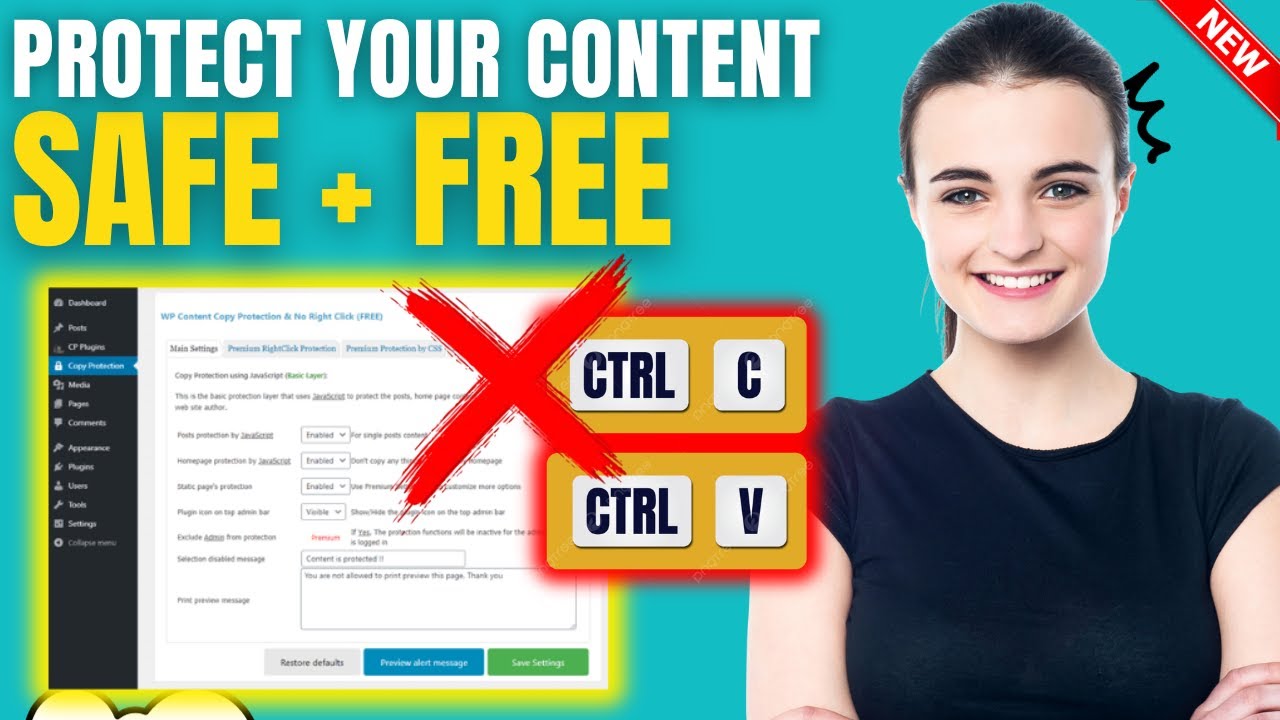
Disable Right-Click
While a simple measure easily circumvented by determined infringers, disabling the right-click function on your website can deter casual content theft. This prevents users from easily copying text or saving images directly from your web pages.
Though not foolproof, this basic step can add a layer of friction for less technically inclined individuals attempting to copy your piece of content quickly.
Content Locking
Implement plugins or scripts specifically designed to prevent high-quality content from being easily copied and pasted. These tools can disable text selection, prevent right-clicking, or even introduce JavaScript overlays that obscure content from automated scraping tools.
While these measures can be bypassed by determined individuals, they effectively deter casual copying and raise the bar for those attempting to steal your work.
Encryption
Encryption secures your content by converting it into a coded format that can only be accessed or read by those who possess the correct decryption key.
By encrypting files, videos, or documents, you ensure that even if the data is intercepted or accessed without authorisation, it remains unintelligible and unusable. Strong encryption algorithms, such as AES-256, provide robust protection against hacking and unauthorised access.
Implementing encryption is essential for safeguarding sensitive information, preventing data breaches, and ensuring that your content remains secure during storage and transmission across networks.
Digital Rights Management (DRM)
Digital Rights Management (DRM) systems control how digital content is used and distributed. By embedding DRM into your content, you can restrict unauthorised copying, sharing, and modification.
DRM technologies work by encrypting the content and requiring users to obtain a license or key to access it. This ensures that only authorised individuals can view or use the content under predefined conditions, such as limited device access or time restrictions.
DRM is widely used in industries like publishing, music, and software to protect intellectual property, deter piracy, and maintain revenue streams by enforcing usage policies effectively.
| Content Protection Tool | Anti-Copying Technique | Benefits |
|---|---|---|
| Disable Right-Click | Prevents basic copy actions | Easy to implement, deters casual theft |
| Copy Protection Scripts | Disables text selection and paste | Provides a stronger barrier against copying |
| Digital Watermarking | Embeds identifiable marks | Helps trace and verify original content |
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Legal Protection Strategies for Digital Content

Protecting your digital content starts with knowing copyright law. This law gives creators special rights to their work, stopping others from using it without permission.
To get the most protection, register your work with the right authorities. This step creates a public record of your ownership, helping you fight back if someone uses your work without permission.
It’s key to protect your intellectual property rights in today’s digital world. These rights let you decide how your content is used, shared, and changed online. By standing up for your rights, you keep your work safe and stop others from using it without asking.
Content licensing is another smart move. These agreements let others use your work but keep you as the owner.
Creative Commons licenses, for example, let you share your work while still keeping some control. By picking the right license, you can share your content while protecting your rights.
- Register your work with the U.S. Copyright Office.
- Understand and assert your intellectual property rights online.
- Choose the right content licensing option to control usage.
Using these legal strategies keeps your digital content safe. It also makes sure your rights as a creator are respected in the changing online world.
Essential Website Settings to Prevent Content Copying
Keeping your website safe is key to protecting your content. Setting up the right settings can stop unauthorised copying. This boosts your website’s security.
Configure .htaccess File Settings
Changing the .htaccess file helps prevent hotlinking. It stops other sites from linking to your images and resources. This way, you control who can access your content.
Implement robots.txt Directives
Robots.txt directives let you decide what search engines can see. Setting it up right helps manage who can access your content. It keeps sensitive info safe from public eyes.
Set Up Content Access Controls
Setting up access controls, like member-only areas, keeps your content safe. Only those with the right password can see it. This adds an extra layer of security to your website.
| Setting | Purpose | Benefit |
|---|---|---|
| .htaccess Configuration | Prevents hotlinking of resources | Reduces bandwidth theft and unauthorised use |
| robots.txt Directives | Controls search engine crawling | Protects sensitive content from being indexed |
| Content Access Controls | Restricts access to authorised users | Enhances security for premium content |
Digital Fingerprinting and Content Authentication Methods To Protect Your Online Content
Protecting your digital content is key. You need strong ways to verify it. This ensures you can prove you own it and spot any unauthorised use.
Digital fingerprinting gives your content a unique ID. This makes tracking and verifying ownership easier. It adds subtle markers that can be found without changing how the content is used.
Digital signatures are also vital. They use secret codes to check if your content is real and unchanged. By signing your work, you ensure it’s safe from tampering.
Blockchain for content protection offers a new way to keep things safe. It records who made and owns your content on a shared ledger. This makes your content secure and transparent.
- Content Verification: Ensures ownership and authenticity.
- Digital Signatures: Validate the integrity of your content.
- Blockchain for Content Protection: Provides decentralised security and tamper-proof records.
| Method | Description | Benefits |
|---|---|---|
| Digital Fingerprinting | Creates unique identifiers embedded in content. | Easily track and verify ownership. |
| Digital Signatures | Uses cryptography to validate content integrity. | Ensures content has not been altered. |
| Blockchain Protection | Records ownership on a decentralised ledger. | Provides tamper-proof records and enhanced security. |
Monitoring Tools to Detect Stolen Content

Protecting your digital assets is crucial. The right tools can quickly spot and stop unauthorised content use.
Plagiarism Detection Services
These specialised services utilise advanced algorithms to scan the web and compare your content against billions of online sources. They identify similarities, highlight potential instances of plagiarism, and provide detailed reports showing the extent of the copied content.
Many offer various subscription levels catering to individual creators and large organisations, allowing you to tailor the service to your specific needs and budget. They are a valuable resource for protecting your written work and academic integrity.
Content Monitoring Platforms
These platforms provide comprehensive solutions to monitor your online presence and track how your content is being used across the internet. They go beyond simple plagiarism detection by identifying unauthorised republication, copyright infringement, and even brand mentions.
These platforms often include features like image recognition and social media monitoring, offering a holistic view of your content’s usage and helping protect your brand reputation.
Automated Alert Systems
Set up automated alerts to receive notifications whenever your content appears online.
These systems constantly crawl the web and notify you via email or other channels when they detect matches or potential infringements. This proactive approach allows you to address content theft quickly and efficiently.
By setting up alerts for specific keywords, phrases, or even your name, you can stay informed about how your content is being used and take action if necessary.
Monitoring Tools to Detect Stolen Content:
| Tool Type | Description | Benefits |
| Plagiarism Detection | Scans the web for copied text content, comparing it against billions of sources. | Identifies plagiarism, provides similarity reports, helps protect written work. |
| Content Monitoring Platforms | Monitors online content usage, including unauthorised republication and copyright infringement. | Tracks content across the web, identifies misuse, protects brand reputation. |
| Automated Alert Systems | Sends notifications when your content is detected online, enabling rapid response to potential infringements. | Proactive monitoring, immediate alerts, facilitates quick action against content theft. |
Strategies to Combat Content Theft on Various Platforms
| Strategy | Blog Content | Video Content on Streaming Platforms | Images & Graphics in Online Portfolio |
| RSS Feed Management | Display excerpts, not full articles in feed. | N/A | N/A |
| Disable Right-Click/Select | Deter casual copying. | N/A (Use platform-specific download restrictions if available) | Deter casual downloads. |
| Plagiarism Checkers | Use plugins to scan for duplicate content. | N/A | Use reverse image search tools. |
| Copyright Notice | Display prominently on each post. | Include in video description and end screens. | Include on website and within image metadata (if possible). |
| Content Locking | Use plugins to prevent copy/paste. | N/A | Disable right-click; use low-resolution images for display. |
| Platform Tools | N/A | Use copyright tools, Content ID. | N/A |
| Watermarking | On images within posts. | Visible and forensic watermarking. | Visible watermarking; embed copyright in metadata. |
| Monitoring/Searching | Use Google Alerts. | Monitor uploads on platforms, use Content ID matches. | Regular reverse image searches. |
| Download Restrictions | N/A | Disable downloads if possible. | N/A |
| Promote Official Channels | N/A | Encourage viewing on official channels only. | N/A |
| Low-Resolution Images | N/A | N/A | Display low-res versions, provide high-res upon request. |
| Image Licensing | N/A | N/A | Clearly state licensing terms on your website. |
Remember that a multi-layered approach is most effective. Combining several of these techniques will provide the strongest defense against content theft.
What Industries are Most Targeted for Copying Content?
Industries most targeted for content copying are:
| Industry | Type of Content Commonly Copied | Reasons for Targeting |
| News and Media | Breaking news, original reporting, articles, photographs, videos | Timeliness of information, desire to be first to publish |
| Education | Research papers, educational materials, online course content, textbooks | Ease of access, potential for monetisation |
| Entertainment | Music, movies, video games, scripts, character designs | High demand, potential for profit through piracy |
| Software/Technology | Code, documentation, software design, proprietary algorithms | Competitive advantage, saving development costs |
| Fashion and Design | Original designs, clothing patterns, graphics, branding elements | Trend exploitation, fast fashion reproduction |
| Marketing & Advertising | Copywriting, slogans, ad creatives, campaign strategies | Replicating successful campaigns, saving creative costs |
| Photography & Art | Photographs, illustrations, digital art, graphic designs | Ease of reproduction and distribution online |
| Academic/Research | Research papers, dissertations, scientific findings | Reputation building, plagiarism in academic work |
This table provides a concise overview of the industries most frequently targeted for content copying, the types of content typically stolen, and the motivations behind such theft.
It’s important to note that this is not an exhaustive list, and content theft can occur in virtually any industry where original creative work is produced.
What Can You Do If Your Content Gets Copied?
Discovering your content has been copied can be frustrating, but several actions can be taken. The appropriate response depends on the severity of the infringement and your desired outcome. Here’s a breakdown of options:
Direct Contact (Informal Approach):
- Identify the Infringer: Determine who copied your content and locate their contact information.
- Politely Reach Out: Send a polite email explaining the situation, providing evidence of your ownership, and requesting they remove the infringing content. This approach can be surprisingly effective, especially if the infringement was unintentional or due to a misunderstanding.
- Offer a Solution: Suggest options like proper attribution, licensing the content, or a link back to your original work.
DMCA Takedown Notice (Formal Approach):
- Draft a DMCA Notice: If direct contact fails or is unsuitable, prepare a formal DMCA (Digital Millennium Copyright Act) takedown notice. This legal notice informs the infringer’s hosting provider or online platform of the copyright infringement and demands the removal of the copied content.
- Send the Notice: Submit the DMCA notice to the appropriate party. Hosting providers and online platforms have designated agents for receiving these notices.
- Follow Up: Monitor the situation and ensure the infringing content is removed.
Cease and Desist Letter (Legal Approach):
- Consult an Attorney: Consider consulting an intellectual property attorney to draft a cease and desist letter. This formal legal document demands the infringer stop using your content and may threaten legal action if they fail to comply.
- Send the Letter: Send the cease and desist letter via certified mail to ensure proof of receipt.
- Consider Further Legal Action: If the infringer ignores the cease and desist letter, you may need to pursue further legal action, such as filing a lawsuit for copyright infringement.
Platform-Specific Reporting Mechanisms:
Many online platforms (like YouTube, Facebook, Instagram, etc.) have built-in reporting mechanisms for copyright infringement. Use these online tools to report the infringing content directly to the platform.
Consider the Context:
- Minor Infringements: For very minor infringements, such as a short quote properly attributed, you might decide that no action is necessary.
- Educational Use: In some cases, educational use of copyrighted material may fall under fair use exceptions. However, it’s essential to understand the specific parameters of fair use.
Key Considerations:
- Document Everything: Keep records of all communication, evidence of the infringement, and any actions you take. This documentation will be crucial if you need to escalate the situation.
- Seek Professional Advice: If you’re unsure how to proceed or are dealing with a complex infringement, consulting an intellectual property attorney is highly recommended.
What’s Next?
Protecting your digital content from being copied is crucial in online space dominated by content thieves.
Implementing robust copyright protections ensures that your original material remains secure and that you, as the copyright owner, retain control over your creations.
Effective methods such as Digital Rights Management (DRM), watermarking, encryption, access controls, and secure Content Delivery Networks (CDNs) are essential tools to protect your content creation efforts.
These strategies not only deter unauthorised copying but also preserve the integrity of your original source, maintaining the value and uniqueness of your online materials.
Additionally, educating human users about the importance of respecting intellectual property rights fosters a culture of ethical content use.
Bytescare prevents copyright violation through its innovative solution, which is designed to protect digital content using advanced technologies.
By knowing the core functionality of content protection and respecting the rights of creators, you can ethically use online resources. Book a demo to explore how Bytescare can safeguard your digital content.
Ultimately, prioritising content protection not only defends your work but also supports a sustainable and respectful digital environment for all creators.
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
What legal measures can I take to protect my content from being copied?
Several legal measures can protect your content:
Registering your work with the copyright office provides legal proof of ownership and enables you to pursue statutory damages if infringement occurs.
Sending cease and desist letters is a formal way to demand the infringing party stop using your content.
Finally, if necessary, you can file a lawsuit for copyright infringement. Consulting with an intellectual property attorney is crucial for navigating these legal processes.
How can I use digital watermarking to safeguard my original work?
Digital watermarking involves embedding a subtle, often invisible, mark into your content (images, videos, audio).
Visible watermarks deter unauthorised use by clearly identifying the owner. Invisible watermarks, detectable with specialised software, are valuable for tracing the origin of pirated copies and proving ownership in infringement cases.
Various watermarking software and services are available, offering different levels of security and customisation.
What role do copyright notices play in protecting my content?
Copyright notices (e.g., © [Year] [Your Name]) formally assert your copyright ownership. While not mandatory for copyright protection, they serve as a deterrent and inform others that your work is protected.
Including copyright notices on your website, within your content, and on physical copies strengthens your claim and makes it easier to pursue legal action if necessary.
How can I prevent unauthorised use of my content on social media?
Protecting content on social media requires a multi-faceted approach. Utilise platform-specific copyright tools and reporting mechanisms to address infringements. Watermark your images and videos before posting. Include copyright notices in your posts and captions.
Actively monitor your social media accounts for unauthorised use of your content, and promptly report any infringements to the platform. Educate your followers about copyright and encourage them to report instances of content theft.
How can creators protect their AI-generated content from being copied?
The legal field surrounding AI-generated content is still evolving. While traditional copyright may offer some protection, its applicability can be complex depending on the level of human input in the creation process.
Some creators use watermarking and embed metadata to assert ownership and track usage. Licensing agreements and terms of use are also crucial for defining permissible uses of AI-generated content. Staying informed about legal developments in this area is essential.
How to protect website content?
Protecting website content involves a combination of technical and legal measures. Use technical tools like disabling right-click, using content lockers, and implementing copy-protection plugins to deter casual copying.
Clearly display copyright notices and terms of use on your website. Register your website content with the copyright office.
Regularly monitor your website for unauthorised use and take prompt action against infringements using DMCA takedown notices or cease and desist letters.
Employing a robust content management system (CMS) with built-in security features can also help protect your website content from unauthorised access and modification.
Is web scraping legal?
Web scraping, the automated process of extracting data from websites, falls into a legal gray area. While scraping publicly available information is generally permitted, scraping copyrighted content or violating a website’s terms of service is illegal.
Recent court rulings have further clarified the legality of web scraping, emphasising the importance of respecting website owners’ wishes and protecting intellectual property.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.