Key Takeaways:
- Implement effective anti-piracy measures with advanced technology, security patches, and legal actions to block illegal content and access to piracy sites.
- Share intelligence and enforce intellectual property law, safeguarding revenue streams and the creative economy against piracy on creators.
- Leverage tools like Bytescare’s digital piracy monitoring service to continuously monitor online video piracy and ensure high-quality content remains secure.
Online piracy is a big issue for governments, businesses, and content creators today. With digital technologies improving and the growth of the net, pirating methods have emerged and have become more complicated, extending to industries such as intellectual property, media, and entertainment.
Piracy not only leads to financial losses, it is a threat to intellectual property, digital security, and innovation.
This article walks you through the steps on how to protect against piracy.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What is Digital Piracy?
Digital piracy is a term for reproducing, using, or redistributing copyrighted content on the Internet.
Illegal streaming, redistribution, sharing, and downloading of film, music, programs, games, electronic books, and other intellectual properties all fall under digital piracy.
Different from traditional piracies, which entail physical commodities or contraband, digital piracies exist in a borderless arena in which data can be shared, replicated, and made accessible everywhere in the world for minimal in the forms of policing and regulation.
There are different types of digital piracy, for example:
File Sharing: The act of downloading or uploading unauthorised digital media reproductions via peer-to-peer (P2P) networks or file-sharing sites.
Streaming Piracy: Free, unauthorised, streaming of content, using pirated streaming apps, websites, etc.
Cracking and Hacking: Bypassing security mechanisms in programs, such as serial numbers, registration codes, and digital rights systems, in a bid to make paid content freely accessible.
Counterfeit merchandise: Peddling unauthorised reproductions of programs, games, or actual merchandise such as DVDs and Blu-rays.
Spreading of piracy is facilitated by sites which support content-sharing in an unlicensed manner. Although this can be a convenient tool for users to access media, programs, or other content, it deprives creators of an opportunity for earning a living off of it.
The Impact of Digital Piracy
Its reach is wider than monetary losses. While it is true it results in declines in revenues for creators, it has severe implications for industries and for consumers.
Economic Impact
Piracy deprives its creator of income earned on sales of digital content. For example, when a movie, a piece of software, or music is pirated, its creator loses a sale of such a piece of content.
The estimated loss for the whole industry of entertainment is in billions of dollars each year, based on some figures.
Intellectual Property Theft
Piracy is a threat, not just for content, but for intellectual property too. Intellectual properties take a business a large amount of time and effort to make and protect, and it is undermined by piracy.
If there is widespread piracy, there is a demotivating impact on creativity, as creators won’t want to invest on new ventures knowing it can be pirated.
Security Risks
Illicit media and pirated software programs have embedded in them such malicious code as malware, spyware, or viruses.
Downloading pirated content not just makes users a part of an illegal act, it can pose a threat to personal security and device integrity. This can lead to identity theft, data breach, and other cybercrimes.
Erosion of Market Integrity
Piracy erodes market worth for digital content and may interfere with legitimate channels of supply.
If there is a pirated, cost-free alternative of a product in existence, there is a threat of a drop in willingness on the part of purchasers to spend on legitimate equivalents.
This led businesses to make stronger anti-piracy and DRM efforts, which, though needed, can on occasions inconvenience legitimate users.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
How to Protect Against Piracy in Digital Age?
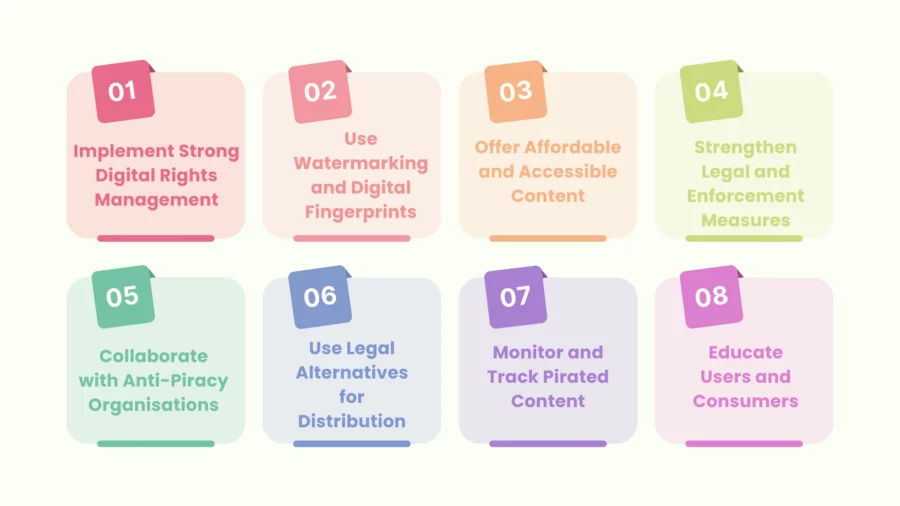
While it is quite unlikely we can completely eliminate piracy, these steps can reduce its frequency and protect digital content.
Implement Strong Digital Rights Management (DRM)
A group of technologies, digital rights management, oversees digital content usage, dissemination, and access.
The unauthorised replication, adaptation, and dissemination of digital content can be controlled using systems of digital rights management. Some of these systems include encryption, watermarking, and authentication of licenses.
While not impenetrable, and occasionally making legitimate users a hassle, DRM systems play a valuable role in curtailing piracy.
For instance, streaming services such as Netflix and Spotify make use of DRM in an attempt to keep users from downloading, and redistributing content in an unauthorized capacity.
Benefits of DRM:
- Prevents unauthorised access and distribution.
- Prevents unauthorised access and dissemination.
- Enables content creators to have ownership of intellectual content.
Challenges of DRM:
- DRM can be circumvented by savvy hackers, which diminishes its effectiveness.
- Some consumers view DRM as an inconvenience, especially when it restricts access to content they’ve purchased.
Use Watermarking and Digital Fingerprints
Watermarking is another digital content security mechanism. Placing an unnoticeable digital watermark or fingerprint in a file allows creators to identify a pirated copy and trace it back to its point of origin, either a distributor or a user.
This is highly effective when pirated content is being exchanged online or via unauthorised channels.
Types of Watermarking:
- Visible Watermarking: A logo or message that is visibly embedded into the media (e.g., a movie with a logo in the corner).
- Invisible Watermarking: Metadata or unique identifiers embedded in the file that are not visible to the user but can be used for tracing.
Watermarking is a piracy prevention tool since it is possible for anyone who intends to pirated to be traced.
Educate Users and Consumers
Education is quite possibly the greatest asset in combatting piracy. Consumers who pirated material may not be aware of the implications, for themselves, and for creators.
Educating users about legal and ethical aspects of piracy can assist in developing a more responsible customer base.
This can be done through:
- Public awareness campaigns.
- Clear communication about the consequences of piracy (e.g., fines, penalties, malware risks).
- Encouraging the use of legitimate streaming or download platforms.
Additionally, offering incentives like discounts, special offers, or exclusive content for legal users can make paying for content more attractive than piracy.
Offer Affordable and Accessible Content
A primary driver for piracy is a lack of cheap, conveniently accessible content. Consumers go for pirated content since legal options cost too much, have geographic barriers, or aren’t conveniently accessible.
Providers of content can combat piracy by pricing content for a modest cost and making it conveniently accessible on a wide array of different systems and devices.
Strategies to Reduce Piracy through Accessibility:
- Global Distribution: Offer content in as wide a geographic spread as is practicable in order not to stimulate demand for pirated copies.
- Affordable Pricing Models: Offer subscription-based services or one-time purchases that are reasonable for consumers.
- Flexible Platforms: Ensure content is accessible on various devices, such as mobile, tablet, and PC, and there is no geographic or device-based limitation.
Strengthen Legal and Enforcement Measures
Legal action and enforcement must ensue in an attempt to deter large scale piracy.
International governments have taken steps in an attempt to pass stricter laws and stricter punishment for online piracy.
Enforced is difficult, though, since it is an anonymous net and there is an international reach of piracy.
Key Enforcement Actions Include:
- Filing Lawsuits: Content creators or companies can take legal action against individuals or websites involved in piracy.
- Website Takedowns: Both governments and corporations can issue takedown notices under statutes such as the Digital Millennium Copyright Act (DMCA) so pirated content can be removed on the web.
- International Cooperation: Since piracy is a global issue, countries need to work together to strengthen laws and share information about pirate networks.
Collaborate with Anti-Piracy Organizations
Anti-piracy organisations, such as the Business Software Alliance (BSA), and the Motion Picture Association (MPA), play an active part in combatting piracy.
The organisations monitor pirated content on the Internet, monitor pirate networks, and coordinate efforts with law enforcement authorities in identifying and closing down pirated operations.
Coordination with such parties can facilitate other sources of support and experience, in case smaller businesses or content creators have not been able to address piracy on an individual scale.
Use Legal Alternatives for Distribution
Instead of relying on traditional channels of dissemination, content creators have alternative avenues directly reaching consumers.
Legitimate options, which include streaming media, online marketplaces, and digital stores, provide creators more ownership of content and income streams.
For example:
- Platforms like YouTube and Twitch offer content creators ways to monetize their work while providing legitimate access to viewers.
- Patreon allows creators to engage directly with their audience and offer exclusive content in exchange for support.
Monitor and Track Pirated Content
Ultimately, content creators have an investment in technology and services aimed at identifying and tracking pirated content.
Some firms have technologies that scan for pirated movie, music, or software content on the Internet. Upon identifying pirated content, such firms send a notice of takedown, among other legal actions, in an attempt to reduce its reach.
Which Anti-Piracy Technology Works for Whom?
Different content types require unique protection measures. Here’s a table summarising different anti-piracy technologies and which industries or types of content they work best for:
| Anti-Piracy Technology | Description | Best Suited For | Key Benefits | Challenges |
|---|---|---|---|---|
| Digital Rights Management (DRM) | Technology that restricts the usage, distribution, and modification of digital content. | Software, Music, Movies, eBooks, Video Games | – Prevents unauthorised copying and distribution. | – Can inconvenience legitimate users. – Often cracked. |
| Watermarking | Embeds invisible or visible markers in digital content to trace its source. | Movies, Music, eBooks, Software, Online Content | – Tracks the source of pirated copies. – Can be used to prove infringement. | – Can be removed or bypassed by advanced pirates. |
| Fingerprinting | Similar to watermarking but focuses on embedding unique identifiers into content. | Video Streaming, Music, Software, Digital Media | – Allows tracking and tracing pirated content back to the source. | – Might not be effective if multiple copies are used. |
| Takedown Notices | Issuing legal requests to remove pirated content from websites. | All digital media, especially video and music streaming sites | – Quick and straightforward action against piracy. | – Not effective if the content is hosted on multiple platforms. |
| Geo-Blocking | Restricts access to content based on the user’s geographic location. | Streaming Services (e.g., Netflix, Hulu), Software Distribution | – Prevents unauthorized access from regions where content is not licensed. | – Can frustrate legitimate users. – VPN workarounds. |
| Encryption | Protects digital content by scrambling data, making it unreadable without decryption keys. | Software, Digital Media Distribution (especially Movies and TV Shows) | – Secures content from unauthorized access. | – Can be bypassed by experienced hackers. |
| Virtual Private Network (VPN) Detection | Prevents access to digital content through VPNs. | Streaming Services, Online Gaming | – Prevents piracy from users hiding their location. | – VPN users can still find workarounds. |
| Anti-Cheat Software | Prevents and detects cheating in video games, ensuring legitimate gameplay. | Video Games | – Prevent piracy through cheating. – Ensures fair play in online gaming. | – Can lead to false positives affecting innocent users. |
| Subscription Models | Provides access to content through a paid subscription rather than one-time purchases. | Streaming Services (e.g., Netflix, Spotify), Software | – Reduces the incentive for piracy by offering affordable access. | – Not foolproof, as users may still seek free alternatives. |
| File-Integrity Checking | Monitors the integrity of digital files to detect unauthorised modifications. | Software, Video Games, Mobile Apps | – Protects against cracks and alterations of software. | – Can be bypassed by skilled hackers. |
| Blockchain Technology | Uses decentralised ledgers to secure and track digital assets. | Music, Art, Intellectual Property | – Provides a transparent and immutable record of ownership. | – Still in early adoption stages. – Scalability issues. |
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What’s Next?
Protecting against piracy requires a multi-faceted approach that incorporates effective anti-piracy measures, legal measures, and advanced technology.
Content owners must collaborate to share intelligence, leverage search engines, and monitor pirate sites hosting illegal content and facilitating illegal sharing.
High-quality content remains a key strategy for enhancing user experience and maintaining revenue streams while discouraging potential pirates.
Intellectual property law and legal implications serve as an invisible mark of protection, safeguarding the creative economy from the threat to content creators posed by Internet piracy and piracy on creators.
Proactive Measure is essential, employing security patches to deter unauthorized use.
Bytescare’s digital piracy monitoring service offers protection for a vast array of digital materials, from movies and music to cutting-edge software.
With advanced AI technology powering its antipiracy programs, Bytescare ensures continuous access to your content while keeping it safe from pirates looking to plunder.
Ready to safeguard your digital realm? Reach out to us or book a demo and fortify your content.
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
How does DRM help in preventing piracy?
DRM, or Digital Rights Management, acts like a lock on your content, controlling who can access and use it.
Can I take legal action against someone who pirates my content?
Yes, if someone is infringing on your copyrighted content, you have the right to take legal action against them.
How can ISPs help in the fight against piracy?
ISPs can monitor and block access to pirated content, making them valuable allies in the fight against piracy.
Are there tools available to detect pirated content online?
Yes, there are several tools and services available that can help you monitor and take down pirated content from the internet.
What benefits does a multi-faceted anti-piracy strategy offer?
A multi-faceted anti-piracy strategy offers comprehensive protection, revenue preservation, and brand integrity. It deters piracy, fosters consumer trust in legitimate products, and provides valuable data insights to inform future actions, ultimately enhancing the overall effectiveness of content protection efforts.
How can content owners protect their revenue streams?
Content owners can protect revenue streams by diversifying income sources, implementing strong copyright measures, engaging directly with audiences, and creating exclusive content. Utilising data analytics for audience insights and exploring partnerships can also enhance loyalty and reduce reliance on single revenue channels.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.

