Key Takeaways:
- Cybercrime is broad, while cyber fraud focuses on deception for financial gain.
- Cyber-enacted crime often exploits vulnerabilities through advanced attacks, whereas cyber fraud primarily uses social engineering tactics.
- Comprehensive cybersecurity solutions, including advanced threat detection and anti-fraud software, are vital to defend against both.
The digital age has undoubtedly provided many useful tools that make life simpler. Unfortunately, this same digital age has birthed a myriad of crimes which have come to be known as cyber crimes and cyber fraud.
Although these two terms are often used interchangeably, they are very different in nature, scope, and impact.
To protect one’s assets, it is important to know the difference between cybercrime and cyber fraud.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What is Cybercrime?
Cybercrime refers to any criminal activity that utilise a computer or network as the target or the instrument to commit the crime.
The level of crime “cyber,” carries out can vary from hacking, malware distribution, identity fraud to complex cyber terrorism.
Those who commit cybercrimes are usually classified under a broader umbrella of people intending to cause disruption or have some ulterior intent behind extracting information or simply trying to create chaos.
The aspect of cybercrimes is that they are rampant and people easily get away with it due to a lack of regulation.
Cyber criminals may be induced by motives that aren’t just financial. They also don’t have any restriction to target specific people.
People ranging from everyday citizens to organisations to entire governments can be objective to these crimes with the advent of the internet.
Categories of Cybercrime
Cyber crime can be broken down into several categories, including but not limited to:
- Hacking and Unauthorised Access: Gaining unauthorised access to systems or networks to steal sensitive data or disrupt operations.
- Malware and Ransomware Attacks: Deploying malicious software to damage systems or hold data hostage.
- Distributed Denial-of-Service (DDoS) Attacks: Overloading servers with traffic to render services unavailable.
- Identity Theft: Stealing personal information for fraudulent purposes.
- Online Harassment and Cyberstalking: Using digital platforms to intimidate or harass individuals.
- Intellectual Property Theft: Stealing proprietary data or copyrighted material.
Characteristics of Cybercrime
Cybercrime encompasses a wide range of illegal activities that are conducted using computers or the internet. Below are some qualities of cybercrime:
Use of Technology – The illegal acts of cyber crime are committed with the help of computers, networks, and the internet.
Anonymity – Criminals are able to conceal their identities as they operate from different parts of the world. This makes it difficult for law enforcement agencies to catch them.
Global Reach – An offender can execute a cyber crime from any location in the world, which means that an attempt can be made to victimise a person in different countries. This makes jurisdiction and enforcement very complex.
Variety of Methods – These may include hacking, phishing, distributing of malware, social engineering, denial of service attacks and many more.
Targeting Individuals and Organisations – Individuals are targeted for identity theft and online scam, while organisations can be victims too through corporate espionage or ransomware attacks.
Financial Motivation – Cybercrime is committed with the financial intention of stealing money, sensitive information, or even the intellectual property of someone.
What is Cyber Fraud?
Cyber fraud refers to the fraudulent uses of the internet and telecommunication systems for personal financial gain.
Like all frauds, it seeks to get monetary profit through deception. It includes phishing, impersonation, online scams, and many other practices where victims are deceived to provide sensitive data such as bank account details and credit cards.
Cyber fraud is a type of cyber crime, but with a keen focus on financial fraud which focuses on tricking an individual into trusting or using a fake system without them knowing how deeply fake it truly is.
Types of Cyber Fraud
Cyber fraud comes in many forms, manipulation of digital systems and even the user’s psychology are exploited. Here are several popular examples of cyber fraud:
- Phishing Attacks: Phishing Attacks: This is a form of social engineering fraud that targets users through emails to steal their personal details such as passwords, user IDs, and credit card numbers.
- Online Shopping Scams: Fake online shops that purport to sell goods or services to unsuspecting clients who are lured with attractive pricing deals only to fail to deliver the goods or services.
- Click Fraud: This type involves generating fake clicks on online advertisements, which artificially inflates costs for advertisers and skews marketing analytics.
- Inventory Fraud: Here, fraudsters manipulate product data to deceive buyers, leading to disrupted operations and impacted sales.
- Investment Scams: Fraudulent schemes that mislead individuals into investing in bogus financial ventures.
- Identity Fraud: The use of a person’s private information to create fake accounts or perform unauthorised transactions.
- Ransomware: Ransomware attacks involve installing malicious software that blocks a user’s files and requests a ransom to unlock them, effectively “kidnapping” the entity’s data.
- Account Fraud: Account takeovers happen when a hacker illegally accesses a user’s account in order to gain sensitive information, redeem loyalty points, or withdraw funds from his/her bank. These takeovers can be prevented by implementing strong policies.
- Purchase Fraud: Purchase fraud is when criminals make illegal purchases using other people’s information. The acts of card cracking and carding are commonly used to execute these purchases.
- Social Media Fraud: Online fraudsters build bots that manipulate the online numbers to give a false sense of buzz or presence and push certain policies. Such fraud can impact public opinion and shape online activities.
- Business Email Compromise (BEC): Targeting companies by spoofing legitimate email addresses to authorise fake transactions.
Characteristics of Cyber Fraud
Cyber fraud is a specific type of cybercrime that involves deceitful practices conducted online to gain financial or personal benefits. Here are some key characteristics of cyber fraud:
Act of Deceit: Cyber fraud is the act of deception where a trick is played to obtain information or finances from the victim through impersonation, phishing, and other forms of deceit one way or another.
Monetary Gain: Most often, the aim of committing fraud is to gain some sort of monetary benefit, whether it be by direct robbery, executing false transactions, or obtaining confidential data which can be sold.
Application of Technology: Usually a fraudster would want to use technology for committing fraud through the use of websites, emails, social medias, and mobile applications.
Exploiting Those at a Disadvantage: Those who are less knowledgeable about technology or tend to be more weak like senior citizens are usually the main targets of most cyber fraudsters due to their carelessness towards online frauds.
Disguised Identity: Operating under fake names or identity is another known method carry out cyber frauds. It hinders the capability of victims of the crime or law enforcement to seek justice making them far more superior than the aforementioned parties.
Use of Fraud Websites and Email Addresses: Making up fraudulent websites or email addresses in a shifty manner to look as if they are from a reputable source is one approach cyber criminals tend to use more.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
The Difference Between Cybercrime and Cyber Fraud
Though both cybercrime and cyber fraud occur in the digital realm, their scope, intent, and impact differ. Below are the key differences between the two:
| Aspect | Cybercrime | Cyber Fraud |
|---|---|---|
| Definition | A broad term for illegal activities involving computers or networks. | A specific type of crime aimed at financial gain through deception. |
| Scope | Includes activities like hacking, malware attacks, cyber terrorism, etc. | Focuses specifically on deceptive practices for monetary gain, such as identity theft or phishing. |
| Primary Goal | Varies – can be data theft, disruption, or causing harm. | Financial gain through deceitful means. |
| Types of Activities | Hacking, phishing, malware, ransomware, DDoS attacks, cyberterrorism. | Phishing, fake websites, credit card fraud, identity theft, online scams. |
| Impact on Victims | Can affect organisations, governments, or individuals; wide-reaching consequences. | Primarily affects individuals and businesses through financial loss or personal data theft. |
| Legal Framework | Governed by broader cybercrime laws, including hacking and cyberterrorism. | Governed by financial fraud laws, identity theft, and consumer protection regulations. |
| Penalties | Often severe, including jail time, large fines, and international collaboration for prosecution. | Financial penalties, restitution to victims, and possible jail time for the perpetrators. |
| Example | Data breaches, large-scale system hacks, ransomware attacks. | Fake online stores, Ponzi schemes, identity theft, fraudulent investment schemes. |
| Targeted Entities | Governments, corporations, large-scale organisations, or individuals. | Individuals or small to medium-sized businesses seeking financial gain through deception. |
| Tools Used by Perpetrators | Malicious software, hacking tools, malware, phishing. | Deceptive websites, fake communications, social engineering techniques. |
Who is Most at Risk of Cybercrime and Cyber Fraud? A Detailed Comparison
| Group/Individual | More at Risk of Cybercrime | More at Risk of Cyber Fraud |
|---|---|---|
| General Public (Individuals) | Tech-savvy individuals: More likely to be targeted by hackers and malware, especially if they use insecure devices or networks. | Elderly and vulnerable people: Often targeted by phishing scams or deceptive offers, due to lack of familiarity with digital threats. |
| Small Businesses | Lack of security infrastructure: Small businesses are often easy targets for cybercriminals using ransomware or DoS attacks. | Limited awareness: Small business owners may fall for phishing scams or BEC attacks, believing them to be legitimate business transactions. |
| Large Corporations | High-value targets: Big companies store vast amounts of sensitive data and intellectual property, making them prime targets for hacking, data breaches, and espionage. | Internal fraud: Fraud can also happen from within through phishing or BEC attacks aimed at employees who are not trained in identifying fraud attempts. |
| Government Agencies | Political and espionage motives: Governments are frequently targeted for hacking, cyber espionage, and DoS attacks. | Fraudulent government schemes: Fraudsters may impersonate government representatives to deceive citizens into providing money or personal information. |
| Consumers of Online Shopping | Exposed to hacking and data breaches: Shopping on insecure websites or platforms increases the risk of personal and payment data theft. | Phishing, fake reviews, and scams: Shoppers are at risk of encountering fraudulent sellers or fake listings that steal money without providing goods. |
| Financial Sector (Banks, Fintech) | Target of data breaches: Cybercriminals often target banks to steal sensitive financial data or carry out fraud (e.g., account takeovers). | Investment fraud and fake financial offers: Customers may be tricked into investing in fake financial products or providing their login credentials to fraudsters pretending to be from legitimate institutions. |
| Employees (Across Industries) | Phishing and malware attacks: Employees are at risk of social engineering scams, which can lead to compromised systems or malware infections. | Business Email Compromise (BEC): Employees, especially those handling finances, are often targeted by fraudsters who impersonate senior management to authorise fraudulent transactions. |
| Frequent Internet Users | Higher exposure to cyber-enabled crime: Regular internet usage increases exposure to malware, hacking, and phishing attempts. | More susceptible to scams: High internet use also means increased chances of encountering fraudulent offers, fraudulent emails, and online scams. |
| Online Service Providers (e.g., Cloud, Hosting) | Data breaches and targeted hacking: These platforms are often high-value targets for cybercriminals looking to access user data or exploit service vulnerabilities. | Fake service offers: Fraudsters may create fake services or exploit hosting platforms to launch fraudulent schemes. |
| Online Content Creators (Influencers, Bloggers) | Impersonation and account hacks: Influencers and bloggers are vulnerable to hacking and impersonation to tarnish their brand or steal their followers’ data. | Fraudulent sponsorships: Content creators may be targeted by scammers offering fake business deals, sponsorships, or investments. |
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
How Cybercrime and Cyber Fraud Affect Businesses and Individuals?
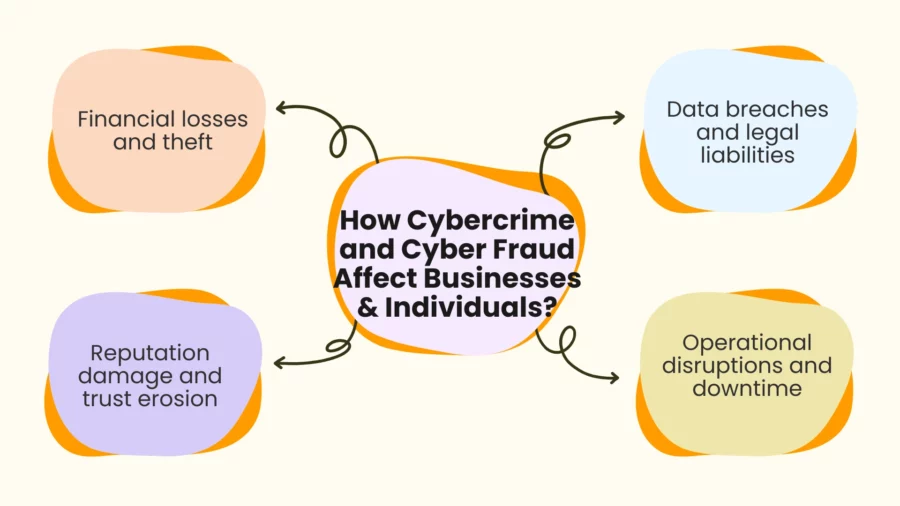
Businesses and individuals the world over face serious challenges that can threaten their very existence. With a little probing further, we can figure out its impact:
Financial Losses
As far as cyber crime and cyber fraud is concerned, the most notable and revenue related losses is directly associated with financial loss.
In the most simplistic terms, it is as devastating as a business money being lost to hackers or having their sensitive data defrauded.
For individuals, financial damage can result from loss in the form credit card fraud or even being a target to identity thieves.
Loss in Brand Equity
In this day and age, it is quite common for a business to suffer from loss of brand equity.
With aliens threatening the cyber borders through cyber crimes, one single attack can undermine decades worth of reputation that a firm might have worked towards accumulating.
Such organisations can suffer a complete loss of trust from their customers and business associates which can take years to recover from. Many organisations have termed such incidents as long term structural symptoms of loss.
Legal and Regulatory Challenges
Cyber criminals and fraudsters present a clear legal and compliance risk to any organisation that falls prey to their schemes.
There are laws, such as GDPR (General Data Protection Regulation) for the European Continent or CCPA ( California Consumer Privacy Act) for the US that place the onus of safeguarding user data on organisations. A breach would mean expensive legal battles and fines.
Preventing Cybercrime and Cyber Fraud
Preventing cybercrime is a hassle and to make things easier, I think we can split it into two chunks – the technical and physical approach.
Below are the effective measures that stand out in terms of minimising the prevention efforts:
Security Measures for Individuals
- Use unique, strong passwords for every account and enable multi-factor authentication.
- Be cautious of phishing emails, phone calls, or messages that ask for personal information.
- Regularly monitor your bank and credit card statements for any unusual activity.
- Install antivirus software and ensure your devices are updated with the latest cyber security patches.
Security Measures for Businesses
- Encrypt sensitive data both at rest and in transit to protect it from unauthorised access.
- Train employees on recognising phishing attempts and using secure practices for accessing company data.
- Use firewalls, intrusion detection systems, and secure VPNs to protect against digital attacks.
- Regularly back up data and create a disaster recovery plan to mitigate the impact of ransomware and other cyber attacks.
What’s Next?
In the evolving digital environment, knowing the difference between cybercrime and cyber fraud is critical for safeguarding economic security and digital resources.
Cybercrime encompasses a broad range of malicious activities targeting accessible computers and electronic devices—from volumetric attacks and login credential theft to cybercriminal attacks exploiting network security.
Cyber fraud, however, specifically leverages social engineering tactics, deceptive email communication from unknown senders, and manipulation of authentication credentials, often targeting individuals with common scams involving gift cards and fraudulent online resources.
Organisations can counter these threats by deploying comprehensive solutions such as advanced threat detection software and anti-fraud software, which enhance device visibility and protect devices from attacks.
By integrating advanced cybersecurity solutions with comprehensive threat detection, businesses can mitigate the effects of cybercrime on businesses and prevent dangerous cyber fraud attacks.
Legal consequences for cyber threat actors are severe, and a fraud report is essential to track and combat cybercrime effectively. The persistent evolution of cyber attacker behavior calls for continuous monitoring and robust measures to safeguard both individuals and the broader online environment.
Bytescare helps protect your digital world from the dangers of cybercrime by offering state-of-the-art solutions to secure your data and digital identity.
Don’t wait until it’s too late—explore our advanced protection tools and get a head start in defending your online presence. Take control of your cybersecurity now. Book a demo now to secure your digital future!
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
How do cybercriminal attacks differ from cyber fraud attacks?
Cybercriminal attacks encompass a wide range of illegal activities, including hacking and data breaches, often motivated by various goals. In contrast, cyber fraud specifically targets financial gain through deceitful practices, such as phishing and identity theft, focusing on tricking victims into providing sensitive information or money.
What role do advanced threat detection software and anti-fraud software play?
Advanced threat detection software identifies potential threats in real-time using machine learning and behavioral analysis. Anti-fraud software focuses on detecting fraudulent activities by analysing transaction patterns. Together, they enhance cybersecurity, enabling organisations to respond quickly to threats and protect against both cybercrime and cyber fraud.
How does credential theft relate to these cyber threats?
Credential theft involves unauthorised acquisition of usernames and passwords, often through phishing or malware. It is a critical vector for both cybercrime and cyber fraud, enabling attackers to access sensitive accounts, impersonate victims, and conduct unauthorised transactions, leading to identity theft and financial loss.
Why is monitoring cyber attacker behavior important?
Monitoring cyber attacker behavior is essential for early cybersecurity threat detection, effective incident response, and gathering threat intelligence. It helps organisations identify potential attacks before they escalate, adapt defenses, and comply with regulatory requirements, ultimately enhancing overall cybersecurity and protecting sensitive data.
How do malicious websites and unknown senders contribute to cyber fraud?
Malicious websites mimic legitimate sites to deceive users into providing personal information, while unknown senders often deliver phishing emails containing links to these sites. Both tactics exploit trust, tricking victims into compromising their security and leading to significant financial loss and identity theft.
What are the legal consequences of cyber fraud?
Cyber fraud carries significant legal consequences to deter malicious purposes. Legal consequences include criminal charges, resulting in fines and imprisonment, as well as civil liability where victims may sue for damages. Regulatory penalties may also apply to organisations failing to protect data, leading to reputational harm and loss of business opportunities.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.



