Key Takeaways:
- Use DRM technologies to control access, usage, and distribution of your content, ensuring that only authorised users can access it.
- Embed watermarks in your digital images and videos to deter unauthorised use and clearly display copyright notices to inform others of your ownership rights.
- Foster awareness about copyright challenges and best practices within your business connections, encouraging a culture of respect for intellectual property and lawful content usage.
In the digital era, protection of digital content has become a very important concern for creators, businesses, and individuals.
Digital content is such an asset that ranges from articles, videos, and images to software and music, which can easily be copied, shared, and distributed.
Although the internet has opened new frontiers for the creators of content, at the same time, the same internet has exposed their works to the piracy, theft, and unauthorised use that threaten them.
Knowing how to protect digital content means understanding how to safeguard intellectual property and monetise works.
The following article outlines strategies, tools, and best practices in digital content protection that will help you protect your intellectual property in the digital space.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Digital Content and Its Vulnerabilities
Digital content is a generic term describing any type of information that is represented in electronic format. Examples include:
- Documents (e.g. Word files, PDFs)
- Multimedia: images, videos, audio files
- Software and applications
- Databases
- Proprietary business information
Common Vulnerabilities
Some of the risks that digital content is susceptible to include:
Cyberattacks: Malware, ransomware, and phishing are used to hack into things.
Data Breaches: There are databases and storage systems that can be targeted by cyberattacks, which result in the exposing of sensitive content, bringing serious financial and reputational damage.
Accidental Loss: It can be further caused by human error, hardware failure, or natural calamities.
Piracy: Digital content is easily copied and distributed illegally, thereby threatening the creator’s revenue and control over their work.
Unauthorised Access: Poor passwords and poor access controls lead to unauthorised access by people who are not supposed to access sensitive content.
What is the Importance of Digital Content Protection?
Among the most vital concerns a person can imagine is the protection of digital content. Creating the best content requires much effort, time, and sometimes resources.
If not protected, it can be easily copied, altered, or sold by people other than its owner, which reduces its value.
Most importantly, theft in a very competitive digital market can result in financial loss, brand damage, and devaluation of a creator’s reputation. Also involved in protecting digital content is keeping control of its distribution and use to ensure it is not abused beyond the confines of the creator.
Content protection allows the following: It holds the rights to intellectual property, which the creators can maintain for their work.
Maintain Copyright Ownership: Ensures creators retain their intellectual property rights.
Prevent Piracy: It prevents piracy or illegal distribution of content.
Lock in revenue streams: This preserves the content’s ability to earn money.
Brand Reputation: Keeps the integrity and authenticity of the content intact.
Encouraging Creativity: Creators are most likely to create more and innovate when their works are secured. A sound protection framework facilitates an environment where creation can thrive.
Protection Through Legal Recourse: Effective digital content protection lets the creators exercise legal action towards copyright infringement, making it possible to actually work against unauthorised uses and find a ground for justice.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
How to Protect Digital Content?
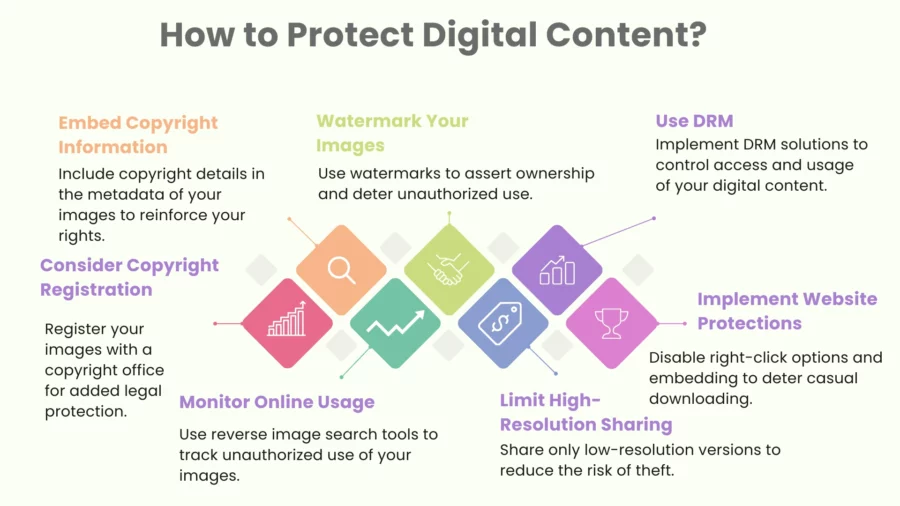
Copyright and Legal Protection
One of the first steps to protection involves creation of legal rights over digital content. Copyright give exclusive rights to the creators for reproduction, distribution, and display of the content.
Here is how protection through copyright helps.
- Automatic Protection: For many countries, copyright protection is now taken to arise immediately after a work is created. However, there are some reasons why you would want to register the copyright with relevant authorities.
- Copyright Registration: Even though the copyright protection is automatic, the registration of your work at the copyright office will add an extra layer of protection. It will create evidence within the public record of the copyright and will be very important if one day you have to go to court to enforce your rights.
- International Protection: Copyrights are the concern of international law, with the involvement of treaties such as the Berne Convention, that ensure protection is available in more than one country. If you intend to distribute your work internationally, you certainly want to familiarise yourself with the copyright laws in other countries.
Digital Rights Management (DRM): Controlling Usage
The term refers to a set of technologies meant for controlling how digital content is accessed and shared and how it is distributed.
DRM solutions are widely used in the media, publishing, and software industries for the purpose of restricting unauthorised use.
Examples of common techniques used in DRM include:
- Encryption: DRM encrypts the content to make it inaccessible to unauthorised users without proper keys. This is useful in digital music, movies, and software.
- Watermarking: Invisible watermarks can be inserted into digital content for source-tracking purposes. In case of any leak or piracy, such a leak may be traced by a watermark.
- Licensing and Authentication: DRM systems can apply restrictions on licensing, whereby the users have to log in to their accounts to gain access to the content. It is used by eBook sellers and subscription-based services.
- Copy Protection: DRM is able to restrict or block the copy of digital content. An example is preventing screenshot or screen recording capabilities during the viewing of content.
While DRM serves well to protect content, it is important to note that some users tend to view it as a limit to usability. As such, it is prudent to ensure a proper balance between content protection and a good user experience.
Watermarking and Invisible Markers: The Digital Signature
Watermarking is a technique that involves embedding a unique mark or signature into a piece of digital content to identify the creator and track usage.
There are two types of watermarking:
Visible Watermarking: A logo, text, or symbol, usually visible, appears on the face of the content. It will more often happen to images, videos, and photographs. In such contexts, the positioning of the watermark can be done very intelligently without giving any hint for removal by cropping.
Invisible Watermarking: This is the methodology of embedding information in the content, which is not visible to the naked eye but can only be found by using special software. Invisible watermarks are used to generate high-value content, such as premium videos or eBooks and software.
Watermarking does serve a number of purposes:
Attribution: It helps users identify the original creator or source of the content.
Anti-Piracy: It acts as a deterrent for those who might want to steal or share content illegally.
Tracking: Should the content get leaked, then the watermarks can help trace the source of leaks by allowing for remedial action.
Licensing Agreements
Another important method of protecting digital content involves licensing. A license is described as an agreement which shows how and under what conditions a third party will be allowed to use the material.
The licensing agreements could be tailor-made to suit particular needs, and it may include terms such as:
Duration: The period the third party is granted the use of the content.
Geographic scope: It describes the area limitation on geographical locations where the material is to be used or distributed.
Exclusivity/Non-Exclusivity: This will outline whether the license is exclusive, whereby no one other than the licensee shall access the content, or non-exclusive, whereby multiple persons could use the content.
Content Usage Restrictions: This is what the licensee can and cannot do with the content in regard to modification, redistribution, or any commercial use.
The licensing agreement serves as a legally clear and binding tool, both to avoid misusing content and to assure that the creator will receive remuneration.
Encryption: Locking Down Access
Encryption is one of the most powerful tools in digital content protection, especially when sensitive or high-value data is involved.
Encryption changes content into unreadable format by using a certain algorithm.
Only with a key or password will the said content be decrypted, which would ensure that only the authorised user or users can actually access the original file.
Encryption is widely used in all types of digital content.
Digital Media: The video and audio files are at times encrypted against piracy.
Software: Most of the software and games use encryption for not being copied or distributed without authority.
Documents: These are documents that might contain very sensitive information; hence, encryption into PDF or Word can prevent unauthorised access.
Encryption can be very strong for content, but its key management needs to be very secure. The best encryption methods do not help without a proper decryption key.
Tracking and Monitoring Content Use
Active monitoring is the only way to monitor and track unauthorised use or distribution. There are several ways of tracking content:
Content Tracking Services: Through platforms like Google Alerts, content creators can track where their content appears online. These tools can help identify instances of plagiarism, unauthorised publication, or content theft.
File Use Monitoring: Certain monitoring tools are designed to report back to originators of the software or of media files, whenever the latter access and/or distribute these kinds of digital files.
Online monitoring services enable creators of content to know how and where their content is used.
Analytics Tools: Analytics platforms, such as Google Analytics or social media monitoring tools, may help trace how the content is being shared and where it appears. Such tools give insight into whether the content is being illegally distributed or pirated.
User Education and Awareness
While technical solutions are important for content protection, educating the users and other stakeholders is likewise important.
Educating your audience about respecting intellectual property rights can reduce the chances of your content being illegally shared or being used without prior permission.
Strategies that are important here include:
Display Copyright Notices: You can give notice that your work is copyrighted and by law, reproductions of your work are not allowed. You should place a copyright symbol and your name on all your content: websites, videos, images, and more.
Robust Terms of Service: Defining Permissible Use: Clearly outline the terms of service for accessing and using your content. Specify what constitutes permissible use and explicitly prohibit unauthorised downloading, distribution, and modification.
Audience Engagement: Engaging with your audiences provides a relationship and community, not just content. A loyal audience will be very much less likely to commit theft and distribution of copyrighted works because such fans value their artist.
Staying Ahead of the Curve
The digital market changes every day. So do the ways by which content protection is breeched. Inked below are just a few more of the available methods that have been used so far for protection of digital content.
Low-Resolution Previews and Streaming: Limiting Download Quality:
Providing low-resolution previews enables customers to review your work without the customer being able to get a quality version of your full work. In the same vein, streaming video and audio rather than offering a download also makes it difficult for people to obtain high-quality versions.
Disable Right-Click and Copy-Paste to Deter Casual Copying: Although these functions can easily be bypassed through other means by anyone who is determined enough, disabling these on your site may help make casual copying difficult to do and further raise the awareness of your copyright restrictions.
Secure File Hosting and Delivery: Protect the Distribution Channel: This will involve the use of reputable file hosting sites that have set in place relevant security and access controls. It is further enhanced by download limits, password protection, and access logs.
Dynamic Content Generation: Making Life Tough for Scraping Bots: Dynamic generation of content rather than serving static files for a website makes the job tough for any automated scraping tool to copy large amounts of information.
Monitoring and Tracking: Routinely search for unauthorised uses of your content on various online platforms using search engines, social media monitoring tools, and specialised piracy-detection services.
Stay Informed: Keep updated about the latest developments in the fields of content protection technology and legal frameworks. Attend industry conferences, read appropriate publications, and consult experts.
Community Building: Engage with your audience and encourage them to report instances of piracy. Community building may prove to be one of the best ways to deter infringement of your work.
Platform-Specific Strategies for Protecting Digital Content
| Platform | Challenges | Opportunities | Strategies |
| Social Media Platforms (e.g., Instagram, Facebook, Twitter) | Designed for sharing, making control difficult; Easy screenshotting and screen recording; Rapid spread of online content. | Wide reach and audience engagement; Platform-specific copyright tools (e.g., Rights Manager on Facebook); Built-in analytics for tracking. | Watermarking (visible and invisible); Utilise platform privacy settings (e.g., private accounts, restricted sharing); Clear copyright notices in descriptions and posts; Regular monitoring for unauthorised use; Reporting infringement to platform; Engaging with audience and encouraging reporting of piracy. |
| Learning Management Systems (LMS) (e.g., Moodle, Canvas, Blackboard) | Maintaining control within closed environments; Preventing downloads and sharing among students. | Built-in access control features (e.g., student logins, course enrollment restrictions); Integration with DRM systems; Tracking student activity. | Restricting download options; Limiting access to enrolled students; Integrating DRM for enhanced control; Utilising platform’s analytics to monitor access and activity; Implementing plagiarism detection tools. |
| E-commerce Platforms (e.g., Shopify, Etsy, Gumroad) | Preventing unauthorised redistribution after purchase; Protecting downloadable products. | Secure payment gateways; Customer account management; Digital product delivery systems. | Limiting downloads per purchase; Setting expiration dates on downloads (where applicable); Using encrypted download links; Watermarking digital products; Integrating with DRM solutions for enhanced control; Monitoring for resale on other platforms. |
| Video Sharing Platforms (e.g., YouTube, Vimeo) | Ease of downloading and re-uploading; Content ID systems not always foolproof. | Content ID systems for automated copyright protection; Monetisation options; Large potential audience. | Registering original content with Content ID; Utilising platform’s copyright tools; Choosing appropriate licensing options (e.g., Creative Commons); Watermarking video content; Engaging with community and reporting infringing uploads. |
| Streaming Platforms (e.g., Spotify, Netflix, Amazon Music) | Preventing unauthorised recording/ripping; Controlling access across devices. | Subscription-based model; DRM integration; Platform-controlled distribution. | Relying on platform’s DRM and security measures; Limiting concurrent streams; Monitoring for unauthorised redistribution; Legal action against circumvention tools and services. |
| Personal Websites/Blogs | Maintaining control over server and online content; Preventing unauthorised scraping and downloads. | Direct control over website functionality; Ability to implement custom security measures. | Disabling right-click and copy-paste (as a deterrent); Implementing password protection for premium content; Using secure file hosting and delivery; Dynamically generating content; Utilising website analytics to monitor traffic and downloads; Watermarking images and other media. |
Remember that the best strategies will depend on the specific platform, the type of content, and your individual needs and resources. Regularly review and update your approach to stay ahead of evolving threats and platform changes.
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What’s Next?
In an era marked by an increase in copyright infringement and the vast amounts of digital media content being created, protecting your digital content has never been more critical.
Creators face significant challenges as accessible content protection solutions become essential in safeguarding their work.
A balanced approach to content security is necessary, employing a breadth of strategies that include robust solutions against piracy and proactive action against infringers.
User -friendly platforms can simplify the implementation of these protective measures, allowing creators to focus on their craft rather than worrying about unauthorised use. By leveraging effective tools and technologies, creators can ensure their digital content remains secure while still reaching their audience.
To take the first step in protecting your digital assets, book a demo today to see how Bytescare can safeguard your digital content and let you rest easy. With its many features designed specifically for creators, Bytescare is here to protect the things that mean most to you in a digital world, allowing you to create with confidence and peace of mind.
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
What are the best practices for copyrighting digital content?
Best practices for copyrighting digital content include promptly registering your work with the appropriate copyright authorities to establish legal ownership. Use clear copyright notices and watermarks to assert your rights and deter infringement.
Implement Digital Rights Management (DRM) to control how your content is used and distributed. Regularly monitor online platforms for unauthorised use and take swift action against infringers. Additionally, educate yourself on copyright laws and leverage user-friendly platforms to streamline the protection process, ensuring your digital media content remains secure.
How can digital rights management (DRM) help protect my online content?
Digital Rights Management (DRM) helps protect your online content by controlling how it is accessed, used, and distributed. DRM technologies can encrypt your content, restrict copying and sharing, and enforce licensing agreements, ensuring that only authorised users can access your work.
What role do watermarks play in protecting digital images and videos?
Watermarks serve as a visual or invisible identifier embedded in digital images and videos. They deter unauthorised use by making it clear that the content is protected and can help trace the source of any unauthorised copies. Watermarks can also enhance brand recognition when used consistently.
How can I secure my website to prevent unauthorised access to my digital content?
To secure your website, consider the following measures:
Use HTTPS: Ensure your website uses HTTPS to encrypt data transmitted between users and your site.
Implement Strong Passwords: Use strong, unique passwords for all accounts and encourage users to do the same.
Limit Access: Use access controls to restrict who can view or edit your content.
Regular Updates: Keep your website software and plugins updated to protect against vulnerabilities.
What are the most effective methods to protect digital content from unauthorised access?
The most effective methods include data encryption to secure content both at rest and in transit, and implementing robust access controls with multi-factor authentication (MFA) to ensure only authorised users can access your data. Utilising Digital Rights Management (DRM) and blockchain technology provides additional layers of security.
Regular security audits and user training also play crucial roles. Leveraging accessible content protection solutions that offers user-friendly platforms that integrate these robust solutions seamlessly, ensuring comprehensive protection against unauthorised access.
Are there legal measures I can take to protect my digital content from piracy?
Yes, there are several legal measures you can take to protect your digital content from piracy. Register your copyrights and trademarks to secure your intellectual property rights. Utilise Digital Rights Management (DRM) to control access and distribution. Implement cease and desist orders against infringers and pursue legal action when necessary.
Stay compliant with data protection regulations and work with legal professionals to enforce your rights. Additionally, using platforms like Bytescare can support your efforts by providing robust protection solutions that complement your legal strategies against piracy.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.

