Key Takeaways:
- Digital Risk Protection Services detect and prevent cyber threats before they can harm your business operations.
- These services protect your brand by identifying potential impersonations, phishing, and other reputational risks online.
- They ensure sensitive business data is shielded from exposure, keeping your digital assets safe from breaches and leaks.
Cybersecurity has become more critical than ever before. With businesses increasingly relying on online platforms, cloud services, and digital tools, the risks of cyber threats have also escalated.
From data breaches to identity theft and ransomware attacks, the consequences of inadequate protection can be devastating. As cybercriminals grow more sophisticated, traditional security measures may no longer be enough to safeguard sensitive data and maintain business continuity.
Enter Digital Risk Protection Services (DRPS)—a proactive approach to cybersecurity that goes beyond conventional methods. DRPS focus on identifying, monitoring, and mitigating digital threats before they can cause significant harm.
Unlike traditional cybersecurity measures, which often react to breaches, DRPS are designed to actively monitor the digital ecosystem, scanning for threats like phishing attacks, brand impersonations, data leaks, and more.
As cyber threats evolve daily, businesses of all sizes—whether large enterprises or startups—must stay one step ahead. DRPS offer an extra layer of protection, ensuring that potential risks are identified and neutralised early.
In a world where digital risks are constantly shifting, businesses must ask themselves: How prepared are they to tackle the unseen risks lurking in the digital landscape?
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
What is Digital Risk Protection (DRP)?
Digital Risk Protection (DRP) is a proactive cybersecurity strategy designed to identify, monitor, and mitigate potential digital threats that can harm an organisation’s reputation, data, and online presence.
Unlike traditional cybersecurity measures, which typically focus on internal network security, DRP expands the focus to include external risks that exist outside an organisation’s perimeter—such as social media, dark web activity, and third-party vendors.
The goal of DRP is to detect threats before they escalate into major breaches or incidents. It involves continuous monitoring of digital channels to uncover potential vulnerabilities, including phishing attacks, brand impersonation, and data leaks.
DRP solutions typically employ advanced technologies like machine learning, AI, and threat intelligence to analyse vast amounts of online data, enabling organisations to quickly respond to emerging threats.
A key component of DRP is brand protection. Organisations rely on DRP to safeguard their brand’s online presence by detecting fraudulent websites, social media impersonations, and malicious content that could damage their reputation.
Additionally, DRP can monitor for sensitive data exposure, including leaked customer information or intellectual property, to prevent exploitation by cybercriminals.
With the digital landscape becoming more complex, businesses are increasingly recognising the need for comprehensive protection beyond traditional firewalls.
DRP helps mitigate risks from all angles, ensuring that organisations are not only securing their networks but also their digital footprint in a connected world.
As cyber threats grow more sophisticated, DRP is essential for safeguarding a company’s assets and maintaining its long-term success.
What Are the Key Components of Digital Risk Protection Services?
| Threat Intelligence | Monitors digital channels for emerging threats like phishing, fraud, and data breaches, providing real-time alerts. |
| Brand Protection | Safeguards the brand’s reputation by identifying instances of brand impersonation, counterfeit sites, and fraud. |
| Data Leakage Detection | Detects exposed or leaked sensitive data across various platforms, including the dark web, to prevent exploitation. |
| Dark Web Monitoring | Scans the dark web for stolen data, credentials, or illicit activities related to your organisation. |
| Phishing Detection | Identifies phishing attempts targeting employees, customers, or the organisation, reducing the risk of scams. |
| Credential and Account Monitoring | Tracks compromised credentials and detects unauthorised access attempts to prevent account takeovers. |
| Social Media Monitoring | Scans social media for fraudulent activity or impersonation of the brand, ensuring the company’s online presence is secure. |
| Vulnerability and Risk Assessment | Identifies and assesses digital vulnerabilities in third-party networks or supply chains to mitigate potential risks. |
| Incident Response and Mitigation | Provides strategies for responding to and neutralising digital threats before they escalate into larger issues. |
| Compliance and Regulatory Monitoring | Ensures adherence to privacy laws and industry regulations by tracking data usage and potential non-compliance risks. |
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
Why Do Businesses Need DRPS?
Protection Against Evolving Cyber Threats
- Businesses today face a constantly changing digital threat landscape.
- Traditional cybersecurity solutions, like firewalls and antivirus software, focus primarily on internal security but often miss external risks.
- Digital Risk Protection Services (DRPS) provide a broader, more proactive approach by identifying and mitigating threats from sources outside the organisation’s perimeter.
- This includes monitoring for cyber-attacks, phishing schemes, brand impersonation, and more, helping businesses stay one step ahead of evolving threats.
Brand and Reputation Protection
- A major concern for any business is its brand and reputation.
- Cybercriminals frequently engage in activities like brand impersonation, setting up fake websites or social media accounts that deceive customers.
- These malicious acts can lead to significant damage to a company’s image, loss of customer trust, and financial consequences.
- DRPS actively monitor digital channels to identify and take down fraudulent websites and social media profiles, protecting your brand and ensuring customer trust is maintained.
Data Security and Privacy
- As data breaches become more frequent and impactful, the need for robust data protection has never been more critical.
- DRPS helps businesses secure sensitive data, such as customer information and intellectual property, by continuously scanning for data leaks or exposure.
- This includes monitoring the dark web, where stolen data is often sold or exploited.
- By identifying these vulnerabilities early, businesses can prevent costly data breaches and safeguard their digital assets.
Ensuring Compliance
- With increasing regulations around data privacy and security, compliance has become a major concern for businesses across various industries.
- Non-compliance can result in hefty fines and damage to the brand.
- DRPS assist organisations in maintaining compliance with regulations such as GDPR, CCPA, and others by monitoring digital activity for any violations or risks of non-compliance, ensuring that your business remains on the right side of the law.
Peace of Mind
- In an increasingly digital world, the risks to businesses are not limited to just internal threats.
- DRPS offer peace of mind by providing continuous monitoring and a proactive approach to cybersecurity.
- With DRPS in place, businesses can focus on their core operations, knowing that their digital footprint is being constantly protected from unseen risks.
What Are the Benefits of Implementing DRPS?
| Proactive Threat Detection | DRPS continuously monitor digital channels, detecting threats like phishing, fraud, and data breaches before they escalate. |
| Brand Reputation Management | Protects the brand by identifying and removing fraudulent websites, social media impersonations, and malicious activities online. |
| Data Security and Privacy | Safeguards sensitive data by detecting leaks or exposure on the dark web and other platforms, preventing potential misuse. |
| Regulatory Compliance Support | Helps ensure adherence to data protection regulations (e.g., GDPR, CCPA) by monitoring and mitigating non-compliance risks. |
| Improved Risk Management | Provides businesses with a clearer knowledge of external risks, allowing for more informed decision-making and proactive mitigation strategies. |
| Minimised Financial Losses | By identifying threats early, DRPS help minimise the potential financial impact of cyber incidents, including legal fees and reputational damage. |
| Enhanced Incident Response | DRPS offer real-time alerts and actionable insights, enabling quicker response and containment of digital threats. |
| Comprehensive Protection | Covers a wide range of risks, including social media threats, phishing, brand impersonation, and dark web monitoring, offering holistic protection. |
| Competitive Advantage | Demonstrates a strong commitment to cybersecurity and data privacy, giving customers confidence and helping businesses stand out in a competitive market. |
| Peace of Mind | Ensures businesses have continuous protection from digital risks, allowing them to focus on growth and innovation without constant worry about security threats. |
Protect Your Brand & Recover Revenue With Bytescare's Brand Protection software
How Does DRPS Work?
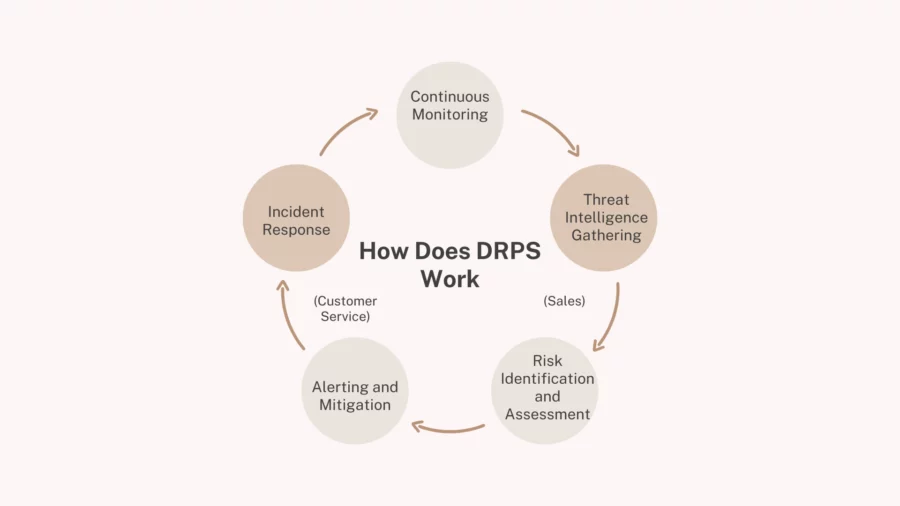
Digital Risk Protection Services (DRPS) work by providing continuous monitoring and real-time threat intelligence across various digital channels, identifying risks before they can escalate into significant issues. The process typically involves several key stages:
Continuous Monitoring
DRPS solutions monitor an organisation’s digital presence across multiple platforms, including websites, social media, the dark web, and third-party networks.
This allows businesses to detect threats in real time, such as phishing attacks, brand impersonation, or unauthorised data exposure.
Threat Intelligence Gathering
Using advanced technologies like machine learning, AI, and threat intelligence feeds, DRPS gather and analyse vast amounts of data to detect patterns of suspicious or malicious activity.
These tools help identify emerging threats, track cybercriminal behavior, and provide insights into the tactics used by attackers.
Risk Identification and Assessment
Once threats are detected, DRPS assess the level of risk associated with each one. This includes evaluating the severity of potential damage, whether it involves brand reputation, data breaches, or regulatory violations. Risk assessments are used to prioritise actions and resources for mitigation.
Alerting and Mitigation
When a threat is identified, DRPS services send real-time alerts to relevant teams within the business.
These alerts are actionable and come with recommendations for mitigating the risk, such as taking down fraudulent websites, securing compromised credentials, or addressing data leaks.
Incident Response
If a threat has already impacted the organisation, DRPS assist in responding quickly and effectively to contain the damage, minimise losses, and recover sensitive data.
By providing comprehensive, proactive protection, DRPS help businesses secure their digital footprint against a wide array of threats.
How to Choose the Right Digital Risk Protection Service?
Choosing the right Digital Risk Protection Service (DRPS) is essential for ensuring comprehensive protection against a wide range of digital threats. Here are key factors to consider when selecting a DRPS provider:
Comprehensive Coverage
Look for a DRPS provider that offers broad coverage across various digital channels, including social media, websites, the dark web, and third-party networks. The service should monitor threats like phishing, brand impersonation, data breaches, and unauthorised access across these platforms.
Real-Time Threat Intelligence
Choose a service that provides real-time monitoring and threat detection, ensuring immediate alerts for any suspicious activity. Real-time data allows businesses to act swiftly and mitigate risks before they escalate into significant issues.
Customisation and Flexibility
Each business has unique digital risks, so it’s important to select a DRPS that offers customisable solutions. The service should allow you to tailor alerts, reporting, and monitoring based on your specific needs and industry regulations.
Reputation and Expertise
Consider a provider with a strong reputation and proven expertise in digital risk protection. Look for reviews, case studies, or testimonials from other businesses in your industry to evaluate the provider’s effectiveness and reliability.
Integration with Existing Security Tools
Ensure that the DRPS integrates seamlessly with your current cybersecurity infrastructure, such as firewalls, SIEM (Security Information and Event Management) systems, and vulnerability management tools. Integration can enhance overall security effectiveness.
Scalability
Select a service that can grow with your business. As your digital footprint expands, the DRPS should be able to scale to meet new challenges and evolving cyber threats.
What Are the Challenges in Implementing DRPS?
Implementing Digital Risk Protection Services (DRPS) can offer significant benefits, but there are also challenges businesses may face during the process. Here are some of the common hurdles:
Integration with Existing Security Infrastructure
- One of the key challenges in implementing DRPS is ensuring seamless integration with existing cybersecurity systems.
- Many organisations already have established security measures like firewalls, intrusion detection systems, and SIEM platforms.
- Integrating DRPS with these tools can sometimes be complex, requiring additional resources, time, and expertise to ensure everything works together effectively.
Cost Considerations
- While DRPS offer significant value, the cost can be a concern, especially for small to mid-sized businesses.
- The pricing models for DRPS can vary based on the level of service, coverage, and customisation required.
- Businesses must carefully evaluate the cost against the potential benefits and ROI to ensure that it fits within their budget.
Managing False Positives
- Like any cybersecurity solution, DRPS can sometimes generate false positives—alerts that are triggered by non-threatening activities.
- This can lead to alert fatigue, where security teams become overwhelmed with false alarms, causing them to potentially miss real threats.
- Effective tuning of the system and clear communication are necessary to minimize false positiveares and ensure a focused response.
Resource and Expertise Requirements
- Successfully implementing and managing DRPS often requires specialised expertise.
- Organisations may need to allocate dedicated personnel or work with external consultants to properly configure and manage the service.
- Finding skilled professionals to handle complex security operations can be a challenge.
Evolving Cyber Threats
Cyber threats are constantly evolving, and DRPS solutions need to stay ahead of new tactics and technologies used by cybercriminals.
- Providers must continually update their threat intelligence and monitoring capabilities to effectively respond to emerging risks.
- This ongoing evolution can be challenging for both businesses and service providers.
DIY Tools vs. Professional Services: Pros and Cons
| Aspect | DIY Tools | Professional Services |
| Cost | Generally lower upfront costs, often with subscription-based pricing models. | Higher initial investment, with ongoing fees for managed services and expertise. |
| Customisation | Limited customisation options; may require manual configuration and adjustments. | Highly customisable services tailored to specific business needs, often with expert guidance. |
| Ease of Use | Can be user-friendly with easy setup, but may require technical expertise for effective use. | Typically requires minimal internal effort, as professionals handle setup, monitoring, and response. |
| Scalability | May require manual upgrades or adjustments as the business grows. | Easily scalable to match growing business needs with continuous updates and monitoring. |
| Real-Time Support | Limited or no support; often reliant on user communities or troubleshooting guides. | 24/7 expert support and incident response, with proactive monitoring and threat management. |
| Maintenance | Regular maintenance, updates, and monitoring are the business’s responsibility. | Ongoing maintenance and updates managed by experts, ensuring that systems remain current and optimised. |
| Expertise | May lack in-depth expertise, requiring the business to learn and manage complex threats. | Access to cybersecurity experts with specialised knowledge and experience in handling diverse digital risks. |
| Speed of Response | Slower response times, as internal teams need to identify, assess, and mitigate threats. | Rapid, professional incident response, with threat detection and mitigation handled immediately by experts. |
| Risk Management | Requires manual identification of risks and threats, which can lead to oversight or missed threats. | Comprehensive risk management with continuous monitoring and expert evaluation of digital risks. |
| Compliance | Compliance may require additional tools or manual effort to track and ensure adherence to regulations. | Built-in compliance support, ensuring alignment with industry regulations like GDPR, CCPA, and others. |
Emerging Trends in Digital Risk Protection Services
Emerging trends in Digital Risk Protection Services (DRPS) are shaping the future of cybersecurity by addressing the growing complexity of digital threats. Here are some key trends:
AI and Machine Learning Integration
The use of artificial intelligence (AI) and machine learning (ML) is becoming central to DRPS. These technologies enable the detection of threats at a much faster rate by analysing vast amounts of data in real time.
AI and ML help identify patterns of malicious activity and predict potential risks, allowing businesses to respond proactively rather than reactively.
Dark Web Monitoring Expansion
As cyber threat actors increasingly turn to the dark web for illegal activities, DRPS are placing more emphasis on dark web monitoring. This includes tracking the sale of stolen credentials, sensitive data, and other illicit activities.
Enhanced dark web scanning helps businesses identify leaks, breaches, or potential data sales before they impact their operational efficiency.
Third-Party Risk Management
With the rise of digital supply chains, businesses are increasingly vulnerable to risks originating from third-party vendors.
DRPS are expanding to include comprehensive third-party risk management solutions, monitoring third-party systems and relationships for vulnerabilities that could affect the organisation’s security posture.
Brand Protection and Impersonation Detection
As brand impersonation becomes a common tactic for cybercriminals, DRPS services are enhancing capabilities to protect organisations’ online presence.
These services now offer advanced monitoring of websites, social media, and mobile platforms to detect fraudulent accounts, fake reviews, or counterfeit sites impersonating legitimate brands.
Compliance Automation
With evolving regulatory requirements, DRPS are increasingly integrating compliance automation. These solutions help businesses continuously monitor their digital risks to ensure they remain compliant with ever-changing laws such as GDPR and CCPA, reducing the risk of non-compliance penalties.
What’s Next?
Digital Risk Protection Services (DRPS) are designed to protect organisations from a wide range of external digital threats.
By continuously monitoring digital channels—such as websites, social media, the dark web, and third-party vendors—DRPS help detect and risk mitigation like phishing, brand impersonation attacks, data breaches, and cyber-attack risks.
These services use advanced technologies like AI and machine learning to provide real-time threat intelligence, enabling businesses to proactively address vulnerabilities. DRPS also offer critical support for compliance with regulations, ensuring that businesses stay aligned with data privacy laws.
With digital risk protection solutions, businesses can safeguard their brand, reputation, and sensitive data, while improving overall cybersecurity resilience in a rapidly evolving digital landscape.
Bytescare offers global brand protection services, ensuring your brand is safeguarded from threats worldwide. Whether it’s unauthorised use or trademark infringement, we provide comprehensive coverage across geographical boundaries.
Trust Bytescare for reliable, worldwide brand protection. Contact us today to secure your brand’s future!
The Most Widely Used Brand Protection Software
Find, track, and remove counterfeit listings and sellers with Bytescare Brand Protection software

FAQs
What is digital risk protection software?
Digital risk protection software provides continuous monitoring of digital channels like websites, social media channels, and the dark web to identify and mitigate external threats such as cyber-attacks, brand impersonation, and data breaches, safeguarding a company’s digital presence against potential threats.
Can small businesses afford digital risk protection services?
Yes, small businesses can afford DRPS, as many providers offer scalable, subscription-based models. These digital risk protection solutions can be tailored to fit the needs and budgets of smaller businesses, helping them manage digital risks without significant upfront investments.
How is DRPS different from traditional cybersecurity?
DRPS focuses on monitoring and mitigating external digital risks like social media fraud and dark web threats, while traditional cybersecurity typically protects internal systems from attacks. DRPS provides a broader, more proactive approach to securing digital assets.
What industries benefit most from DRPS?
Industries that rely heavily on digital engagement, such as e-commerce, finance, healthcare, and technology, benefit most from DRPS. These sectors face high exposure to data breaches, brand impersonation, and cyber-attacks, making DRPS essential for protecting digital assets.
How does digital risk protection work?
DRPS continuously monitor digital channels for threats, utilising AI and machine learning to detect and assess risks. They provide real-time alerts and support businesses in mitigating issues like phishing campaigns, data exposure, and brand impersonation to protect their digital footprint mapping.
Why is digital risk protection important?
Digital risk protection is essential for safeguarding a business’s online reputation, customer data, and compliance with regulations. As cyber threats grow more sophisticated, DRPS helps businesses proactively identify and respond to risks, preventing damage and ensuring long-term security.
Ready to Secure Your Online Presence?
You are at the right place, contact us to know more.

